Cracking LM and NT hashes.
Jordi Forès Garcia • December 10, 2022
hacking HackingWindows 0xWord-HackingWindows-PocsWelcome to my post, today we will crack all the hashes we extract from the previous post with Mimikatz, Metasploit, Windows Credential Editor. This is one thing we can do in a pentest when we get this kind of hashes, if the passwords is realy easy we can use the rockyou.txt dictionary and check if we can get a password in plain-text.
The tools that we will use to day are Hashcat and John The Ripper, they are tool focused in the cracking passwords now we will go in detail.
John The Ripper
First released in 1996, John the Ripper (JtR) is a password cracking tool originally produced for UNIX-based systems. It was designed to test password strength, brute-force encrypted (hashed) passwords, and crack passwords via dictionary attacks.
Here we can see the differents attacks :
1. Dictionary Attack: In this type of attack the tool tries passwords provided in a pre-fed list of large number of words, phrases and possible passwords derived from previously leaked data dumps or breaches.
2. Brute-force Attack: In this type of attack, the tool asks the user to configure a few settings, for example, the minimum and maximum lengths the correct password may fall into and what types of characters it could possibly consist of.
3. Rainbow Tables: Because mission-critical and security-oriented applications seldom store passwords in plaintext and instead store their fixed-length hashes, rainbow tables can be efficient especially if a large list of hashed passwords is available is compared against an existing data dump to find the correct password in its plaintext form. Using rainbow tables is faster than brute-forcing as the hashed data is precalculated.
Here we have the hash file which we get from the meterpreter connection in the last post. We just copy-paste the output from hashdump command, now you just have to use one of this tools to get the plain-text passwords.
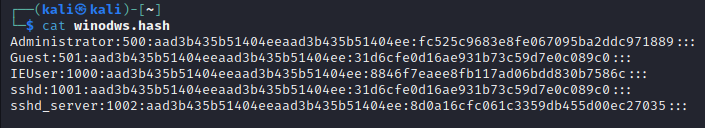
For John The Ripper we just have to indicate the dictionary that we will use to crack the passwords, the file with the hashes and the format that the hashes are. With that will be enough if the passwords are in the dictionary otherwise we have to appeal another tools. For this POC we can see that our hashes are so easy to crack, it took john the ripper a second to get the plain-text passwords.
Hashcat is a password cracking tool used for licit and illicit purposes.
Hashat is a particularly fast, efficient, and versatile hacking tool that assists brute-force attacks by conducting them with hash values of passwords that the tool is guessing or applying. When used for benign purposes, such as in penetration testing one’s own infrastructure, it can reveal compromised or easy to guess credentials.
Hashcat is, however, better known for being used for nefarious purposes. Hackers use Hashcat, readily available for download on all major operating systems, to automate attacks against passwords and other shared secrets. It gives the user the ability to brute-force credential stores using known hashes, to conduct dictionary attacks and rainbow tables, and to reverse engineer readable information on user behavior into hashed-password combination attacks.
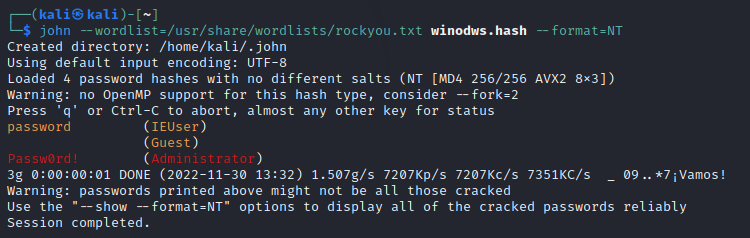
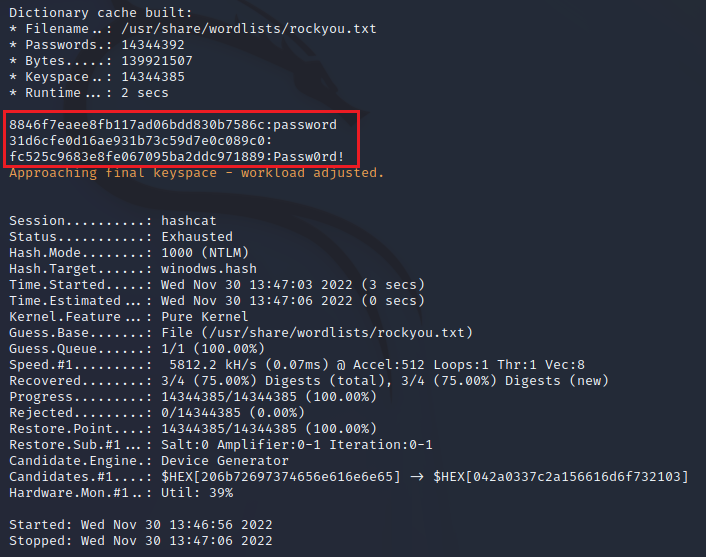
In hashcat we will use the same file to crack the passwords, in the first screenshot we can see in the command that hashcat is a little bit more complicated, thats cause Hashcat have more utilites than John The Rippper. Let's see what this parameters mean...
- -a 0: Indicates the attack mode. For exemple, in this case the 0 mean the dictionary attack.
- -m 1000: The number 1000 specifies the hashes format in particular NT. You can check in the help menu the other fomarts.
- windows.hash: Is the file with all the hashes we wanna crack.
- --username: Indicates that the windows.hash have username in it.
- /user/share/wordlists/rockyou.txt : The dictionary we'll use to the attack.
- --potfile-path: This file will have the cracked hashes.
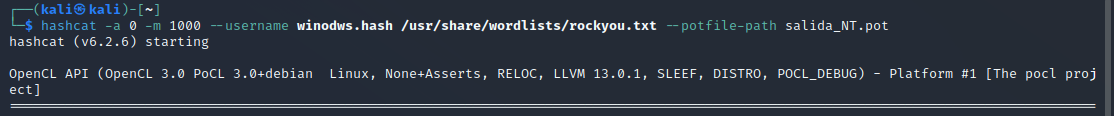
Here we can see the hashes were cracked successfuly and we get the palin-text password. Now we could login with no problem in the user account, if the RDP or SSH port were open we could try to access it.
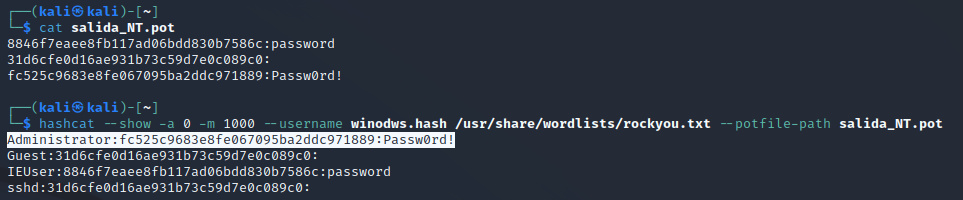
We can read the .pot file that we generated or we can use the --show option to list all the hashes we crack. In this case it was simple cause the passwords were so simple, thats why you have to use a strong password cause if a hacker gets your hash you make them work as hard that they will give up.
I like cryptographi cause it one or if not the most important things we need to navegate through internet without criminatls get our sensitive data. I recomand you to use MFA in all your accounts and have strong password, if you hear one website that you are registred were victim of a cibercriminal attack reset the password inmediatly.
I wish you liked this post and it helps you in one way or other, the next post will be more interesting we'll see the Pass-The-Hash attacks. This attacks are intresting cause we don't need to crack the hash to get access in the user account.
Be safe and don't forget "Effort overcomes talent"