How abuse sdclt.exe to Bypass UAC.
Jordi Forès Garcia • November 19, 2022
hacking HackingWindows 0xWord-HackingWindows-PocsWelcome to one of the parts of the book that I like the most, I recognize that we are still in the first chapter but what I am going to show you here is going to blow your mind.
If you like Windows hacking you are probably familiar with the concept of bypass. What we are going to do during this post is to use some vulnerabilities in the sdclt.exe file. Thanks to these vulnerabilities we will be able to bypass the UAC (User Account Control) and obtain a cmd.exe with high integrity.
To realize this proof of concepts we'll need a Windows 10 with an old version sinces the actual versions have fixed this kind of vulnerabilites so we have no other choise to use this one. Under the screenshot I let you a link to download it so you can reproduce this exercises.
Bypass UAC through App Path
On this occasion we'll talk about another technique, uncovered by Matt Nelson (@enigma0x3). As the previous post, this new technique uses a Microsoft signed binary that has autoElevate set to true.
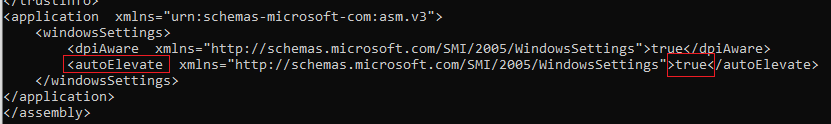
It may only be used for the bypass technique for Windows 10, since in Windows 10, sdclt.exe is self-elevating, but unlike in the case of Windows 7 where the requestedExecutionalLevel directive in Manifest is set to AsInvoker, which will prevent self-elevation . Here we make sure that the sdclt.exe has the autoElevate set to true.
Starting with Windows 7, a clear differentiation is made between applications installed for one user, or for all users of the computer. The applications installed for a user are registered in:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\App Paths.
Those installed for all users are registred under:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\App Paths.
Analyzing the behavior of the binary, you can see how sdclt.exe uses a control panel window to embedded itself. We can see that by the parent PID from the control.exe and comparing it sdclt.exe PID. We check if the control.exe is running in hight integrity, and the last thing we need is know from where is sdclt.exe executing control.exe.
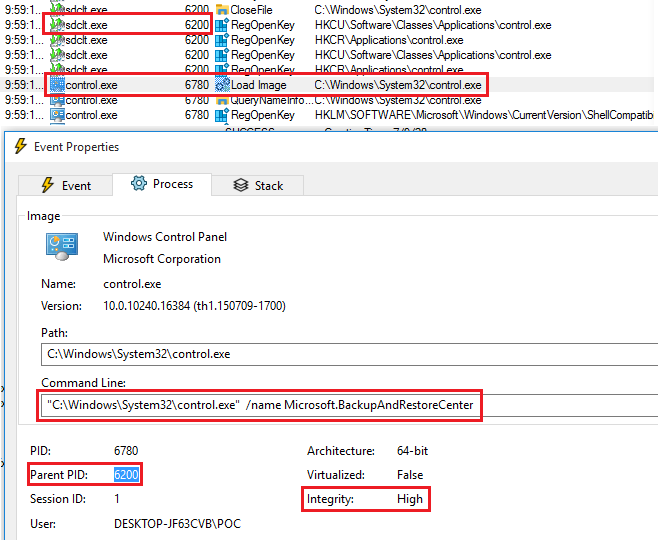
The sdclt.exe binary will get the path to control.exe from the Windows registry, so by monitoring the actions performed in the Windows registry, we are looking for a path in HKCU with the control.exe file and NAME NOT FOUND result. These particular operation have a hight relevance to this type of techniques that can be used to changes his value.
In this case we have these path HKCU:\Software\Microsoft\Windows\CurrentVersion\App Paths\control.exe witch complete all the requests we talk above.
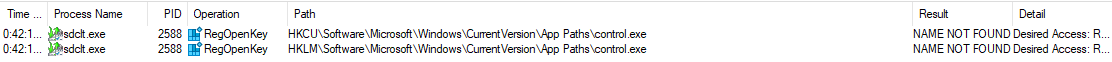
HKCU calls, generated by a process running in a high-integrity context are particularly interesting for this type of techniques. What we want to do is to create this path but insted of executing control.exe we can use cmd.exe. In this case when we execute sdclt.exe and it tries to execute control.exe it will execute our payload cmd.exe.
If everything happens as expected, you will be able to invoke any binary and seeing that sdclt.exe is being executed at a high integrity level, you will have managed to bypass the UAC protection.
To do so let's use regedit.exe to create the path that we want to exploit. We have to add in he control.exe key the value for our payload in my case I'll use cmd.exe but this is up to you.
To simplify all the process, as a proof of concept, Matt Nelson has created the following Powershell script Invoke-AppPathBypass. Now we just need to run the function that we import in our powershell and we can see that it works.
How Microsoft patch this vulnerability ? He just change were the sdclt.exe is installed, HKCU is for apps in your current users thats why we can change the value of it but if we put it into HKLM we stoped getting privileges to change the value and thats how microsoft patch this vulnerability.
Bypass UAC fileless.
For this bypass Matt Nelson probed the sdclt.exe process to see if the program could be run with any parameters that would help raise the integrity of the process. To his surprise, he found the /kickoffelev parameter that allowed him to self-elevate the process and thus achieve a shell with high integrity.
Now we have to find out which path is vulnerable to know where to put our payload. For that we will need the help of procmon with the filters that I will show next.
Una vez configurados los filtros podemos ejecutar nuestro proceso con el parámetro /kickoffelev, para ello me voy a ayudar con Windows+R para ejecutar el programa run y luego escribimos el sdclt.exe /kickoffelev.
Don't panic if you see this error it completly normal, is something that has to do with the sdclt.exe process, has to do with the misconfiguration of the parameter that we added.
We have to spend time looking for, what we need in this case is the HKCU key and the column result has to be NAME NOT FOUND, so that will mean we can abuse this path to get what we want .
Once we have the path that provides command execution we've to create it with regedit.exe to test if we can execute whatever we want.
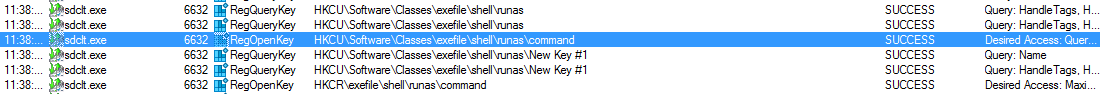
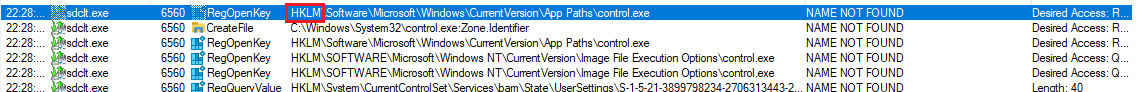
With the path created now we just need to execute the sdclt.exe /kickoffelev and realize that nothing is happening, why this isn't working? Now we have to check procmon again and another path will apear, for this is why I think these bypass is interesting .
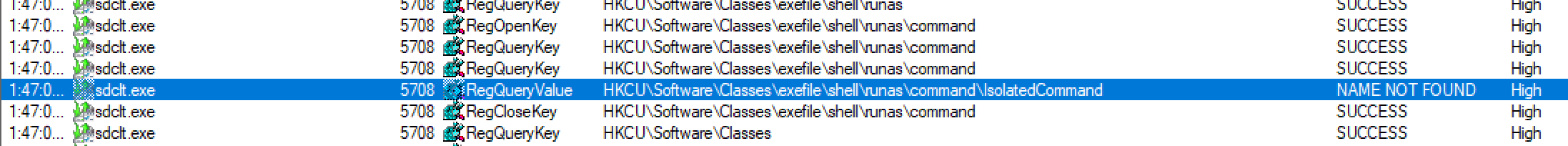
Let's create the path with regedit.exe but this time we have to add a key value with the name IsolatedCommand and his value will be cmd.exe.
For now the only thing that we have to do is execute the sdclt.exe /kickoffelev and wait for the cmd.exe popup.
To simplify all the process, as a proof of concept, Matt Nelson has created the following Powershell script Invoke-SDCLTBypass. Now we just need to run the function that we import in our powershell and we can see that it works.
Another fileless UAC Bypass.
As we know sdclt.exe uses control.exe to get embedded, we can see if control.exe has some paths that we can abuse to get the bypass. To do so, we'll use the procmon to monitor the control.exe process and get the NAME NOT FOUND and the HKCU reg key .
Now that we already know the path we create it into regedit.exe to check if it's vulnerable.
Here happents the same as we saw in the previous bypass, nothing happen when we execute the sdclt.exe and thats cause we still need to add something. To know what we are missing we can use procmon and execute again the sdclt.exe and watch for NAME NOT FOUND paths, this time we can filter by the same path we already have and we can see that now there is another NAME NOT FOUND path, this one ends with DelegateExecution.
So, we execute regedit.exe and create the path, first we try it without any value, let's see what happen.
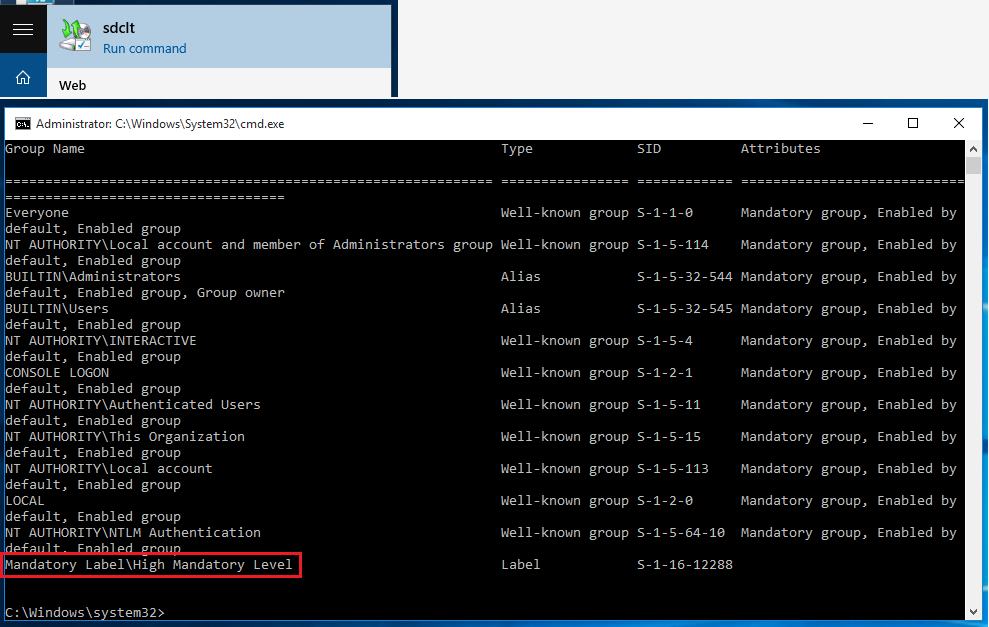
The last thing to do is to execute the sdclt.exe again and cross our fingers. This time we can see the cmd.exe popup, with the command whoami /groups we confirm that we have hight integrity shell.
We can try to modify the Invoke-AppPathsBypass.ps1 script to use it in this case, what we need to change are three things the path for the key we want to add and the values. Invoke-AppPathBypass
Now we can test if our new script is working as spected.
Windows Defender
With the antivirus we can see that it's an old version too because we are working with the last version of Windows 10, jokes aside. We can distinc three types of behavior.
1- The antivirus has not reacted at all that means this version of Windows was vulnerable to it.
2- The antivirus first notify as about the malicous behavior and then stop our cmd.exe, I think this happen cause the antivirus close the process executed by the malicous activity and our cmd.exe is a child from it so if you kill the parent process the child dies too.
3- The antivruis notifies us about the malicous activity and tries to clean it but we can steal use the cmd.exe, and thats cause in this case maybe the cmd.exe is executed as a parent process then when the antivirus kills the malicous parent process the cmd.exe is not part of it.
I hope that you like it what I'm doing , I'm enjoing every second of it doing it and if I can teach you something in the process that means a lot to me. I know this work is from Matt Nelson (@enigma0x3) and is nothing original but I'm learning alot about the topics of Windows Hacking while I'm shareing with you so.
I'm keep working with the exam and with the twitch comunity we have reached an agreement that I will do one exam for each chapter of the book. If you want it when I have it the first one I'll share with you.
And remember that "Effort overcomes talent".